Understanding RADIUS Servers
Learn about the features & benefits of RADIUS servers.
Table of Contents
So what is a RADIUS server, really?
If the RADIUS protocol were a person, it would be an old man shaking his cane and yelling at kids to get off his lawn. RADIUS stands for Remote Authentication Dial-In User Service, which should give you a clue of how long it’s been around (since the early 90’s!) In fact, it was originally designed for organizations like ISPs that had many users connecting remotely via point-to-point serial links (like a dial-up connection) but it has since evolved to provide security for remote access across several types of network connections like VPN, wired, and wireless.
What's the purpose of a RADIUS server?
A RADIUS server is a network device using the RADIUS protocol that handles AAA for your network: Authentication, Authorization, and Accounting. These are 3 key elements of network security:
- Authentication: Are you allowed to use this network?
- Authorization: Ok, you got in the door - what resources are you allowed to use?
- Accounting: How long were you here, and how much data (or other resources) did you use
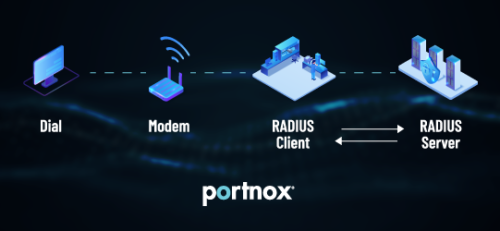
To use RADIUS you need two things:
- A RADIUS server
- An IDP (Identity Provider; basically a directory of user/device information). You need an IDP because the RADIUS server itself does not store any user information. Therefore it needs a directory to check. Common IDPs include Azure AD, Google, & Okta.
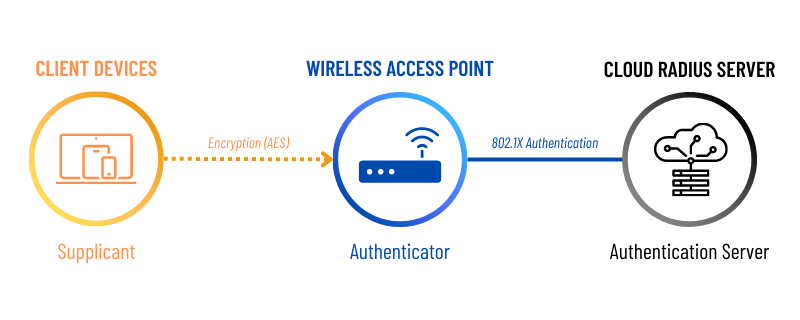
How does a RADIUS server work?
Under the Hood
So what happens exactly when you click “connect”?
- The RADIUS client (that’s your laptop) sends an Access-Request message to the RAIDUS server (this has a username and encrypted password OR has certificate details to compare against the CRL)
- RADIUS server reads the information from the Access-Request & compares it against the IDP (Azure AD, G-suite, etc.)
- If a match is found, the RADIUS server then checks if there is an access policy or profile that matches the user credentials (for instance, if you were in the “HR” group in Azure AD, you would probably have access to salary information and payroll data; if you were in “Finance” you might have access to budgets and quarterly results, etc.)
- RADIUS server will then send an Access-Accept message if everything is all good or it will send an Access-Reject message.
- The Access-Accept message will contain a filter ID and a shared secret. If the shared secret does not match what the client has, the client will reject the message.
- If it does match, the RAIDUS server will then connect the user to the specific RADIUS group depending on the Filter ID.
- RADIUS uses the filter ID to do Role-based authentication.
Table of Contents
Types of RADIUS servers
Cloud-native RADIUS server vs. traditional on-prem RADIUS server
So, having a RADIUS server sounds like a great way to make network secure, why don’t more people use them?
They can be a pain to set up - not super complicated per se, but it’s another piece of network equipment you must install, configure, and maintain. For a long time, security wasn’t a super high focus, and when most of your workforce was connecting via wired connections from one large office, it wasn’t as necessary. However, things look a lot different today - workers are connecting from all over the world with a variety of devices. The ever-growing list of massive data breaches has pushed security far up the list of important things for companies to focus on. The days of a password with a capital letter and a special character being enough are long past.
Thankfully, set up and maintenance does not have to be painful - there are several cloud-based solutions available that are quite easy to configure and maintain. Any network device that does not require after-hours patching windows is bound to be popular with IT folks. Of course, that prompts the question, what if you lose interest access, or worse, your cloud provider goes down? Solutions such as Portnox’s RADIUS-as-a-Service includes a local RADIUS server that you can download and install easily, and it acts as proxy server that caches authentication requests. That way, even when your users can’t get out to the world, they can still access local resources.
Table of Contents
What are the benefits of a cloud-native RADIUS server?
Simple RADIUS deployment
One of the many advantages of cloud-based solutions is how easy they are to set up, and cloud-based RADIUS is no exception. On-prem software feels like “death by a thousand papercuts” - do you meet the system hardware requirements? OS requirements? Do you have to install a new version of .Net? Is there a remnant of an old piece of software that’s conflicting with what you’re trying to install? Thankfully, with cloud-based RADIUS you don’t have to worry about any of that. Set-up is so easy, you could order a pizza and have your network protected by the time it arrives.
Easier RADIUS & directory service integration
Continuing on the ease of use theme, integrating a cloud-based RADIUS server with your existing directory services (like Azure AD, on-prem Active Directory, G Suite, etc.) is also very simple. This is extremely useful for things like letting your end-users self-enroll their devices for network access (less overhead for IT!) And access authentication with existing domain credentials - so someone doesn’t have to have a separate login for the VPN, their workstation, and all the other resources they need. Life is easier for IT and Users - win-win!
Zero RADIUS maintenance
If you’ve ever spent a weekend night doing a software upgrade, praying nothing goes wrong so you can just go to sleep, ignoring text messages from your friends and family who are out having fun - or worse, been in the middle of an extended outage due to an upgrade gone wrong, answering angry Teams messages from your boss while sending silent curses to Bill Gates, Linus Torvalds, and anyone else you can think of, you know how valuable cloud-based RADIUS servers are. Living in the cloud means taking the burden of maintenance off you and your IT team and giving you back your weekends.
Table of Contents
What is RADIUS server?
Types of RADIUS servers.
Benefits of RADIUS server
How to use Cloud-Native RADIUS server
Best Practices for Cloud-Native RADIUS server.
How are some ways to use a cloud-native RADIUS server?
RADIUS authentication & authorization
As we discussed earlier, where RADIUS shines is how well it handles authentication and authorization. Authentication is the basic connection - can you authenticate to the wireless network? The wired network? The VPN? Depending on who your user is and what their job function requires, you can restrict or allow certain network connections. Authorization is what resources you are allowed to access - so the contractor working on the conference room renovation can join the wireless network, but they won’t get access to the finance department’s file server.
RADIUS accounting
RADIUS accounting is a helpful service, but it’s probably not quite what you are thinking of. The word “Accounting” would suggest a full breakdown of a user’s actions while connected and it’s not quite that comprehensive. What it will tell you, though, is how long you’ve been connected and how much data you’ve used. This is super useful if you’re doing any kind of billing based on usage, or trying to figure out who your data hogs are during peak usage times.
RADIUS proxy & roaming
RADIUS proxy and roaming can be set up so that your users can move between different networks without having to get separate logins for each new network - the RADIUS server acts as proxy and just forwards the authentication requests to the new RADIUS server. A great example of this is eduroam - an international Wifi service for users in higher education. A professor from the University of Texas can visit the University of Colorado and log on to the wireless network with the same credentials they use back home.
RADIUS redundancy
RADIUS redundancy has two parts. The first part is making sure your cloud provider has enough capacity to handle times when there are swarms of users logging in - first thing in the morning, during a quarterly meeting, etc. The second part is what happens if your internet is down and your cloud provider is unreachable? Well, in those cases, you can set up a simple-to-install pre-configured on-prem RADIUS backup that will cache all the information from the main cloud RADIUS server, so that if the cloud server becomes unavailable for any reason everyone can still log in. The on-site backup should be pre-configured based on the cloud-based server you already set up, so you get peace of mind with hardly any effort!
Table of Contents
What is RADIUS server?
Types of RADIUS servers.
Benefits of RADIUS server
How to use Cloud-Native RADIUS server
Best Practices for Cloud-Native RADIUS server.
What are best practices for implementing a cloud-native RADIUS server?
Use authorization policies to restrict user access
A key aspect of Zero Trust Network Access is limiting the access users have - not because you don’t trust your staff, but because in the event of compromised credentials, you don’t want a bad actor to wreak havoc across your entire network. Your finance guys don’t need to get into your domain controllers, and your support reps shouldn’t be looking at HR files. A RADIUS server helps you make sure that the right people have access to the right resources to do their jobs, and nothing more.
Use the EAP-TLS authentication protocol and digital certificates
The most common digital certificate is X.509, and EAP-TLS is the most common authentication protocol to enable the use of those X.509 certificates. EAP-TLS is a robust security protocol because it requires an extra level of authentication - not just the user, but the access point as well. This shuts out any MITM (Man in the Middle) attacks and ties your certificate to specific devices so you can be sure that a device is who it says it is.
Use a private certificate authority for certificate-based authentication
Passwords are problematic in lots of ways - either they’re re-used for multiple sites, written down somewhere, never changed, etc.
Certificates are much more secure because they take the users out of it - when you send a request for authentication, the device presents its certificate to the RADIUS server. First the server will check if the certificate is expired. Assuming it's not, then it will compare it to a CRL (certificate revocation list.) If it’s all good there, then you’re in!
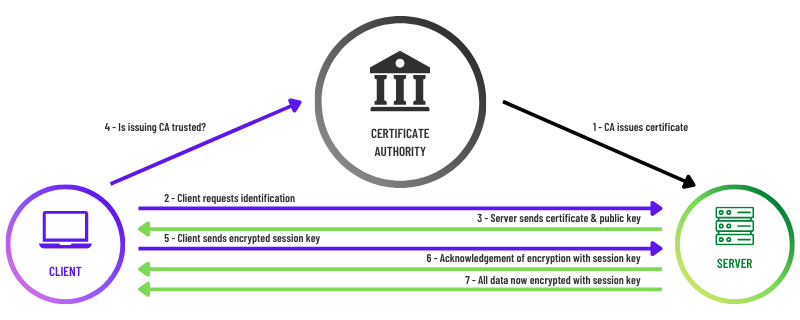
Use server certificate validation
We spoke earlier about the importance of certificates, but it really cannot be overstated. Compromised credentials are responsible for over 80% of all security breaches; no matter how strong a user’s password is or how often they have to change it, it still poses a huge risk. The huge advantage of server certificate validation is that it authenticates the device itself. Using a certificate means that even if a bad actor did get a hold of valid account credentials, they still would not be granted access to the network. And thanks to SCEP, deploying certificates is no longer the labor-intensive nightmare it was before.
Test on wireless networks first
Nothing demonstrates the need for a RADIUS server like corporate WiFI, however. If you have a WiFi network (and who doesn’t?), you probably have one shared password. Take a walk through the office and you’ll see it written on post-it notes, whiteboards, company t-shirts….not exactly secure.
And if a bad actor gets access to your WiFi network, it’s super easy to sniff the traffic on that network (one of the reasons you should never, ever log into your online banking details in a coffee shop, airport, or other public WiFi.) Not to mention what happens if you ever have to change that password, and deal with a never-ending parade of users whose smart phones won’t connect!
RADIUS to the rescue - put a RADIUS server before your Wireless Access Points and you get secure credential or certificate-based access for only the people you want to have access. Plus, no more passwords on post-its!