Prior to the passage of the Digital Operational Resilience Act (DORA), compliance standards for financial institutions across the E.U. were a confusing mess. In an effort to streamline these standards, DORA created a framework for information and communication technology risk management so that consumers could feel safe about who they trusted with their money. Today, NAC is helping companies meet DORA compliance requirements.

NAC solutions play a crucial role in enhancing cybersecurity within organizations by enforcing strict access controls. These controls can help align with DORA regulation cybersecurity objectives by ensuring that only authorized personnel and devices can access critical systems and data. Strong access control is Portnox Cloud’s specialty. Utilizing the 802.1X protocol – the gold-standard for network access protocol – Portnox can deliver robust authentication and authorization across wired, wireless, and VPN connections. For IoT devices that typically don’t support 802.1x, we have IoT Device Trust, which not only fingerprints IoT devices with 96% accuracy but also looks for anomalous behavior to prevent MAC address spoofing. If your security camera starts acting like a laptop, Portnox will alert you and kick it off the network.
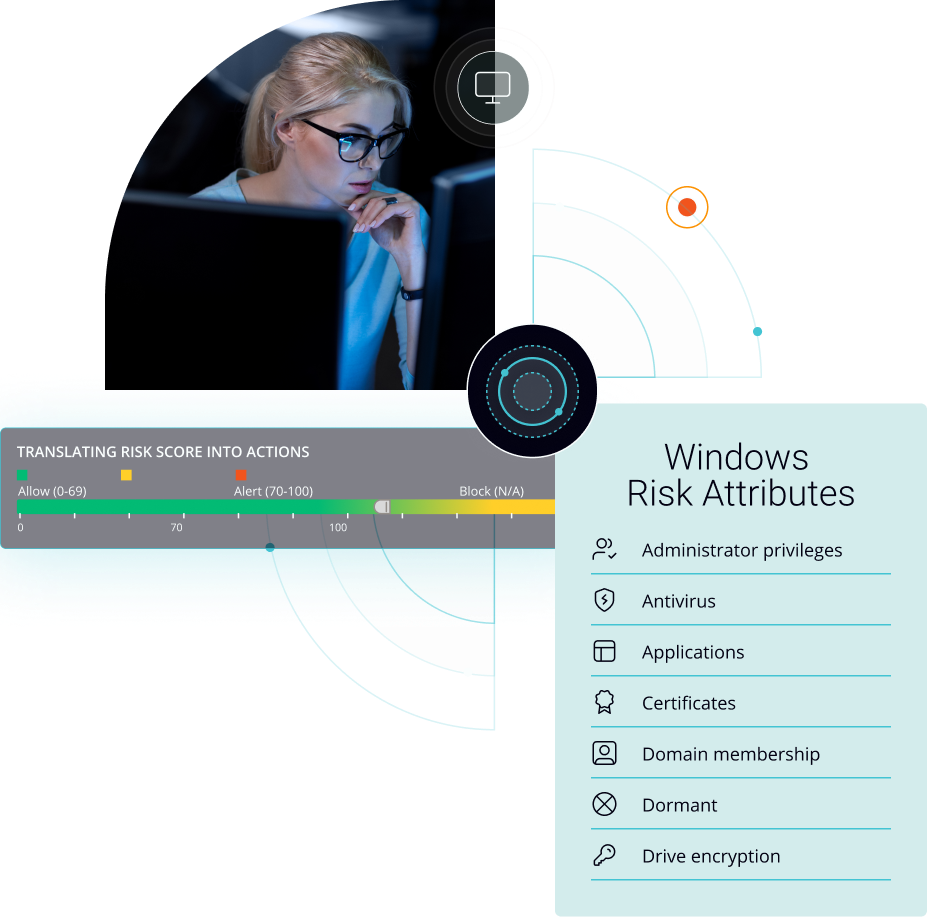
NAC solutions often include features for continuous monitoring and risk assessment of devices connected to the network. This aligns with DORA’s focus on identifying and mitigating cybersecurity risks in the financial sector. NAC can provide real-time visibility into the devices and users accessing financial networks, allowing organizations to detect and respond to security threats more effectively. Portnox not only offers continuous risk assessment based on security policies you create, but we have automated remediation options that will take the guesswork out of access for your users and IT staff. Windows firewall not running? We’ll start it. Unauthorized USB drive? We’ll eject it. You can define policies for a plethora of devices, from smartphones to linux workstations.
DORA imposes specific cybersecurity and operational resilience requirements on financial entities operating within the EU. NAC can help organizations demonstrate compliance with these requirements by providing audit trails, access logs, and other documentation that show how access controls and security policies are enforced. This can simplify the compliance reporting process for financial institutions. Portnox Cloud uses RADIUS for AAA services – Authorization, Authentication, and Accounting, so you can keep track of who is on your network and when. We also offer alerting and reporting options that can provide you an overview of what is happening with your network and let you know of any issues. Portnox Cloud will make sure you are in the know when it counts.
DORA regulation requires financial entities to have robust incident response plans and reporting mechanisms in place. NAC can assist in incident response by quickly isolating compromised devices from the network and limiting the spread of threats. Additionally, NAC can generate reports and logs that can be used for incident documentation and reporting, helping organizations meet their DORA regulation compliance obligations. IoT devices are particularly susceptible to data breaches, and Portnox Cloud’s IoT device trust was created with that in mind. Not only do we have highly accurate IoT Fingerprinting, but if your security camera starts acting like a laptop we can automatically quarantine or completely remove it from the network.
DORA regulation also emphasizes data protection and the importance of safeguarding sensitive financial data. NAC can help protect data by ensuring that only authorized users and devices have access to financial systems and data repositories. It can also prevent unauthorized data exfiltration attempts by restricting the movement of data to and from unauthorized devices. Role-based access is key to making sure your sensitive data is safe – only people who should have access to it will have access to it. Another key aspect is segmentation – making sure that if someone is one part of the network, their movement to other parts is restricted. Portnox Cloud will make sure no one is traveling across your network viewing sensitive data.
NAC solutions often integrate with MFA systems to provide an additional layer of security. DORA recommends strong authentication measures, and NAC can enforce MFA for users accessing financial systems, helping organizations comply with these recommendations. Experts agree simple passwords are not enough – in fact, compromised passwords are responsible for the vast majority of all data breaches. Portnox Cloud can integrate with your MFA systems or even better, help you go passwordless for the best authentication security possible. Certificate-based authentication is phishing and social engineering proof, along with providing a better user experience and saving your IT teams time, and Portnox Cloud makes it easy.
Simplifying things is always a worthwhile goal. Now’s your chance to simplify network access control and fall in line with DORA regulation requirements. Find out how the Portnox Cloud is helping organizations of all sizes revamp and strengthen their access control faster than ever.
DORA Regulation Compliance
DORA compliance emphasizes ICT risk management, incident reporting, resilience testing, business continuity, and oversight of third-party providers. While DORA doesn’t prescribe specific tools, it requires organizations to implement effective controls that reduce risk. Portnox Cloud supports these goals with identity-based access control, real-time device profiling, and continuous posture assessment to reduce exposure to network-based threats.
Portnox Cloud supports DORA compliance by reducing the likelihood of security incidents and operational disruption caused by unauthorized access or risky endpoints. It validates identity, device posture, and policy requirements before granting access, helping financial organizations enforce consistent security controls across distributed networks. This strengthens resilience by preventing compromised endpoints from becoming entry points to critical systems.
Access control is critical for DORA compliance because it limits who and what devices can reach systems that support financial operations. Portnox Cloud enforces least-privilege access across wired, wireless, and remote connections using identity and device posture checks. This reduces attack surface, helps prevent lateral movement, and supports stronger protection of services required for operational resilience.
Operational resilience depends on knowing what endpoints are connected and whether they introduce risk. Portnox Cloud provides real-time discovery and profiling of managed devices, BYOD, and IoT, reducing blind spots that can lead to incidents. This visibility strengthens risk management by enabling organizations to enforce security policies consistently, detect unknown devices quickly, and respond faster to change.
DORA compliance is an ongoing program that requires continuous risk management, monitoring, and enforcement. Financial organizations must maintain effective controls as threats evolve, technologies change, and third-party relationships expand. Portnox Cloud supports ongoing DORA compliance by delivering continuous access policy enforcement, real-time device posture monitoring, and centralized visibility—helping teams stay resilient without heavy operational overhead.
After completing the form, an email will be sent to you with the report download link.