Cloud-native access control now protects you no matter where you’re headed or where you connect from. Portnox ZTNA delivers zero trust application access with fast, passwordless, risk-based authentication and access control for all your business-critical SaaS and on-prem applications.

The last thing your IT team needs is a constant barrage of tickets asking “Why is everything suddenly so slow?!” Yet, other ZTNA solutions provide security at the expense of your network performance.
Portnox ZTNA was designed to provide zero trust application access that is fast, secure, scalable—and did we mention fast? Modernize your remote access without sacrificing productivity.
Let’s face it—passwords are insecure, and MFA is annoying. Both end users and IT teams face issues caused by lax password security measures, leaving systems vulnerable to bad actors who use brute force, phishing, and man-in-the-middle attacks to gain unauthorized access.
Unify your zero trust access control with passwordless authentication across your entire organization, from your network to your apps to your remote connections, and more.
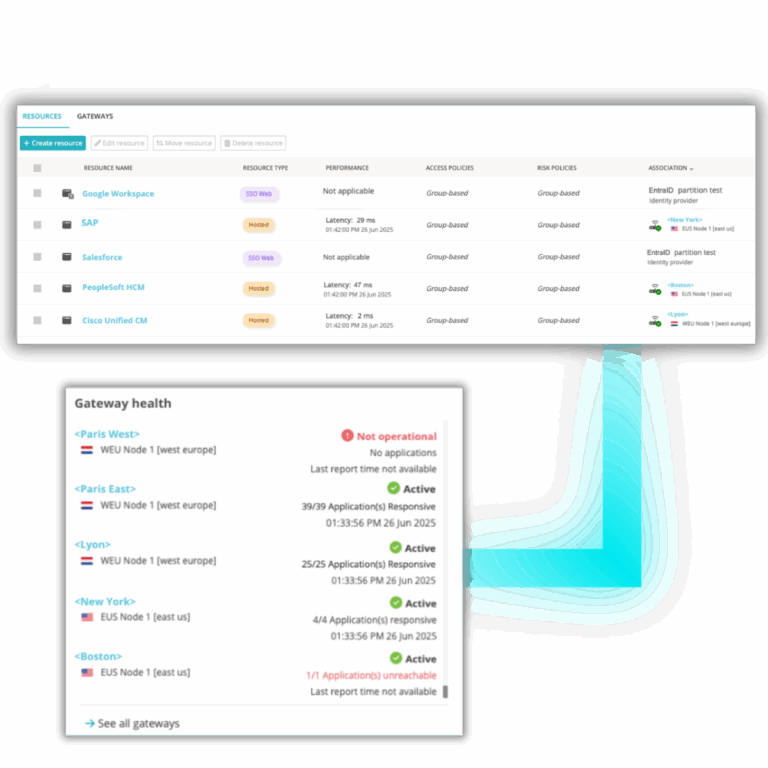
Passwordless authentication is crucial to protecting your assets, but once someone is in, what are they allowed to access? Don’t just give away keys to the castle—segment your network to increase zero trust application access. Implement smart access control policies based on roles, location, and more.
Go a step further with least-privileged access. Make sure people only have access to the resources they need to do their job, protecting you from lateral movements by internal and external threats.
The success of your entire cybersecurity approach hinges on your ability to control risk.
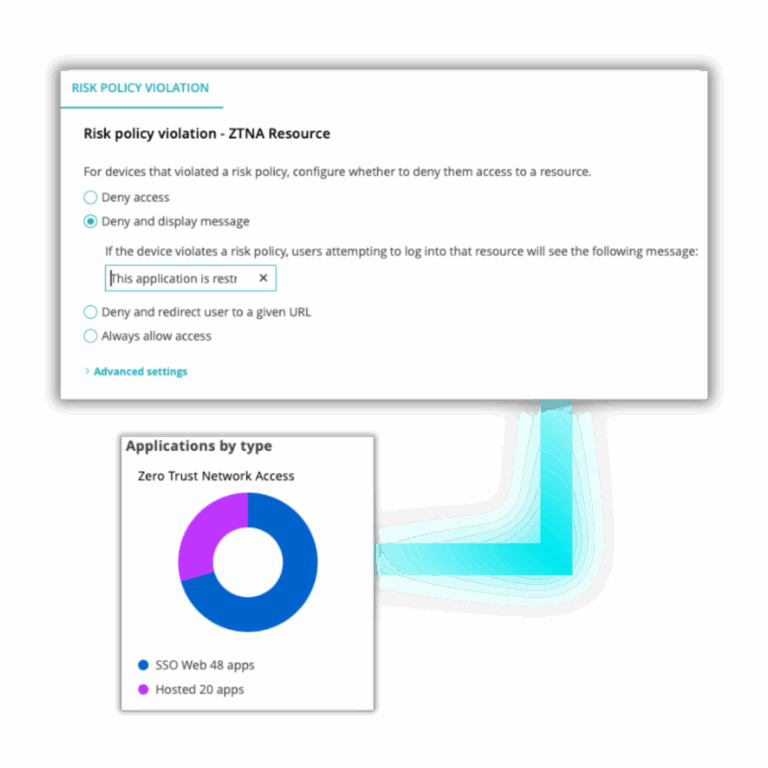
Portnox provides you with the ability to identify devices that pose a threat to your environment. Create policies for any device, make sure antivirus is up to date, check for forbidden software, ensure firewalls are running, and much more. Our robust policy engine will help you mitigate risk, freeing up your IT team for more business-critical tasks.


Staying ahead in IT means strengthening cybersecurity—and zero trust architectures now lead the charge. But let’s face it: embracing zero trust can feel daunting. With so many tools and complexities, it’s easy to lose your way.
To understand how organizations navigate zero trust, Portnox teamed up with TechTarget. We surveyed hundreds of IT and cybersecurity professionals across North America. Discover the insights we uncovered in our Trends in Zero Trust report.
ZERO TRUST APPLICATION ACCESS
Zero trust application access is a security approach that grants users access to specific applications—not the network—based on identity, device posture, and contextual risk. With Portnox Cloud, zero trust application access ensures every request is verified explicitly, least-privilege access is enforced, and users only see the applications they’re authorized to use, regardless of location.
Portnox Cloud delivers zero trust application access by acting as an intelligent access broker between users and applications. It continuously evaluates user identity, device posture, and risk signals before granting access. Instead of exposing applications to the network, Portnox provides secure, policy-driven access at the application level—reducing attack surface and preventing lateral movement.
Zero trust application access differs from a VPN by eliminating broad network access. VPNs place users on the network once authenticated, increasing exposure. Portnox Cloud provides zero trust application access by granting access only to approved applications, enforcing continuous verification, and revoking access automatically when risk changes—resulting in stronger security and a better user experience.
Yes, zero trust application access is purpose-built for remote and hybrid workforces. Portnox Cloud enables users to securely access internal and cloud applications from anywhere without relying on VPNs. By enforcing consistent policies across locations and devices, organizations maintain strong security while enabling seamless access for employees, contractors, and third parties.
Zero trust application access reduces attack surface by ensuring applications are never directly exposed to the network. With Portnox Cloud, users connect only to the applications they’re authorized to access, and nothing more. This limits lateral movement, blocks unauthorized discovery, and prevents attackers from pivoting across the environment—even if credentials are compromised.
Yes, Portnox Cloud supports passwordless zero trust application access using strong, identity-based and certificate-backed authentication. By removing reliance on passwords, Portnox reduces credential theft risk while improving user experience. Passwordless authentication is combined with device posture and risk evaluation to ensure access remains secure and continuously verified.
Zero trust application access improves operational efficiency by eliminating VPN management, reducing access-related support tickets, and simplifying policy enforcement. Portnox Cloud centralizes application access control in a cloud-native platform, enabling IT teams to manage policies, monitor access, and respond to risk in real time—without maintaining complex infrastructure.
After completing the form, an email will be sent to you with the report download link.