The NERC (North American Electric Reliability Corporation) compliance guidelines serve as the backbone for ensuring the security and reliability of the electrical grid. In the face of growing cyber threats, Network Access Control (NAC) plays a pivotal role in supporting NERC compliance from a cybersecurity perspective. By implementing NAC, organizations strengthen their defenses, mitigate risks, and safeguard critical infrastructure, aligning with NERC’s stringent security requirements.

The Portnox Cloud delivers unique access controls, including microsegmentation, for users across all access layers, including wire, wireless and VPN. The platform verifies the identity and security posture of devices and users before granting access to the network. Such capabilities help to prevent unauthorized access and potential security breaches, which is a key objective of the NERC CIP framework.
Portnox delivers an accurate inventory of devices connected to the network, and provides visibility into the types of devices, their configurations, and their compliance status. This information is crucial for implementing the asset management requirements of the NERC CIP framework, which includes identifying critical cyber assets, tracking changes, and monitoring the cybersecurity posture of those assets.
Portnox’s zero trust access control platform can continuously monitor all devices and users connected to the network, checking for compliance with security policies and detecting any anomalies or suspicious activities. This aligns with the NERC CIP requirements for monitoring and logging activities on critical systems and detecting potential cybersecurity incidents.
NAC can contribute to incident response efforts by providing real-time information about the devices and users on the network. In the event of a cybersecurity incident or a breach, NAC can help in identifying affected devices, isolating them from the network, and facilitating incident investigation and containment activities, which is consistent with the NERC CIP framework’s incident response requirements.
NAC solutions often offer features like network segmentation, encryption, and policy enforcement, which can help organizations meet the security controls outlined in the NERC CIP framework. By ensuring that devices and users adhere to security policies and standards, NAC assists in maintaining compliance with NERC CIP regulations.
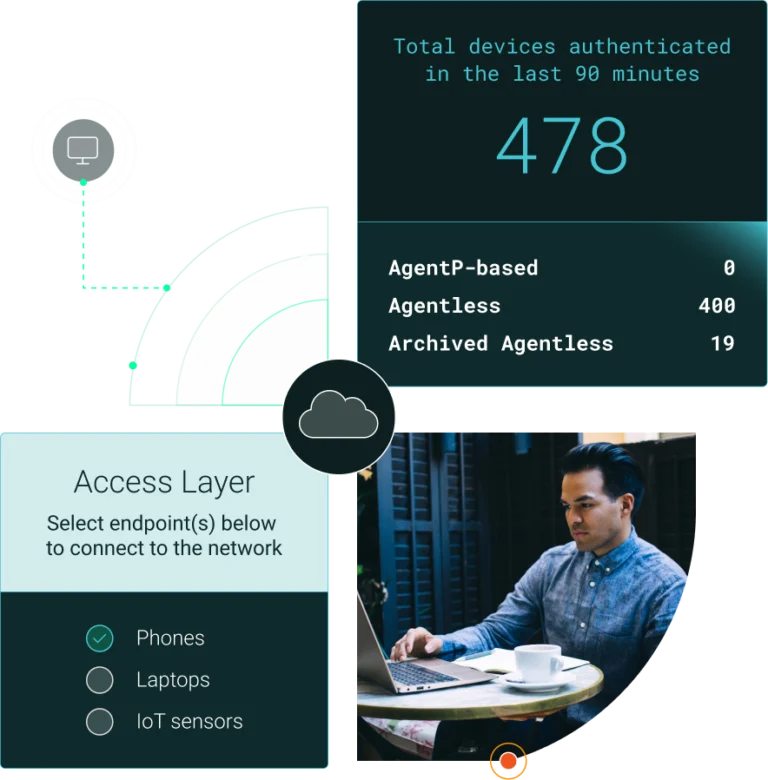
Securing your network will always be a priority, but it doesn’t need to be a drain on time and resources. With Portnox Cloud’s RADIUS solution, companies can now efficiently and affordably authenticate to Wi-Fi, wired switches and network devices, as well as VPN while simplifying administration and enabling long-term scalability.
NERC COMPLIANCE
The NERC (North American Electric Reliability Corporation) standard of security refers to a set of regulations and guidelines developed by NERC to ensure the reliability and security of the bulk power system in North America. NERC is a nonprofit organization that oversees the operation and maintenance of the electric power grid in the United States, Canada, and parts of Mexico.
The primary standard related to security is the Critical Infrastructure Protection (CIP) standards, which are designed to protect the cyber and physical security of the bulk power system. The CIP standards establish requirements for the identification and protection of critical assets, the detection and mitigation of cyber threats, and the response and recovery from security incidents.
The NERC CIP standards consist of several versions, with the latest version being CIP version 5. These standards outline specific requirements for entities responsible for operating and maintaining the bulk power system, such as utilities, transmission companies, and generation companies. The standards cover areas such as access controls, incident response, security monitoring, personnel training, and security awareness.
Compliance with the NERC CIP standards is mandatory for entities that are classified as “critical infrastructure protection” (CIP) entities, which include most utilities and companies involved in the operation of the bulk power system. NERC oversees the enforcement of these standards and conducts audits and assessments to ensure compliance.
The NERC CIP standards establish requirements for cybersecurity in the electric power industry. These standards are designed to ensure the reliability and security of the bulk power system in North America. Here are some key requirements outlined in the NERC CIP standards:
It’s important to note that these are general descriptions of the requirements outlined in the NERC CIP standards. The actual standards are more detailed and comprehensive, covering additional aspects of cybersecurity in the electric power industry. Entities subject to these standards should refer to the official NERC CIP standards documents for specific requirements and guidance.
The specific requirements for network access control are outlined in the CIP-005 standard, which focuses on the establishment and maintenance of an electronic security perimeter (ESP). Here are some key elements of network access control required by NERC:
It’s important to note that these are general descriptions of the requirements for network access control outlined in the NERC CIP-005 standard. The actual standard provides more detailed requirements and guidance. Entities subject to the NERC CIP standards should refer to the official NERC documents for the specific requirements and implementation details.
Here are some key aspects of endpoint security compliance within the NERC CIP standards:
While NERC’s standards provide a framework for addressing endpoint security compliance, it’s important to note that the specific implementation details may vary based on the entity’s risk assessments, size, and operational characteristics. Entities subject to the NERC CIP standards should refer to the official NERC documents and guidance for comprehensive requirements and recommendations related to endpoint security compliance.
After completing the form, an email will be sent to you with the report download link.