Leverage cutting-edge authentication, authorization, and accounting (AAA) services with the cloud-native TACACS+ from the Portnox Cloud to bolster your network device administration and keep your network humming along.

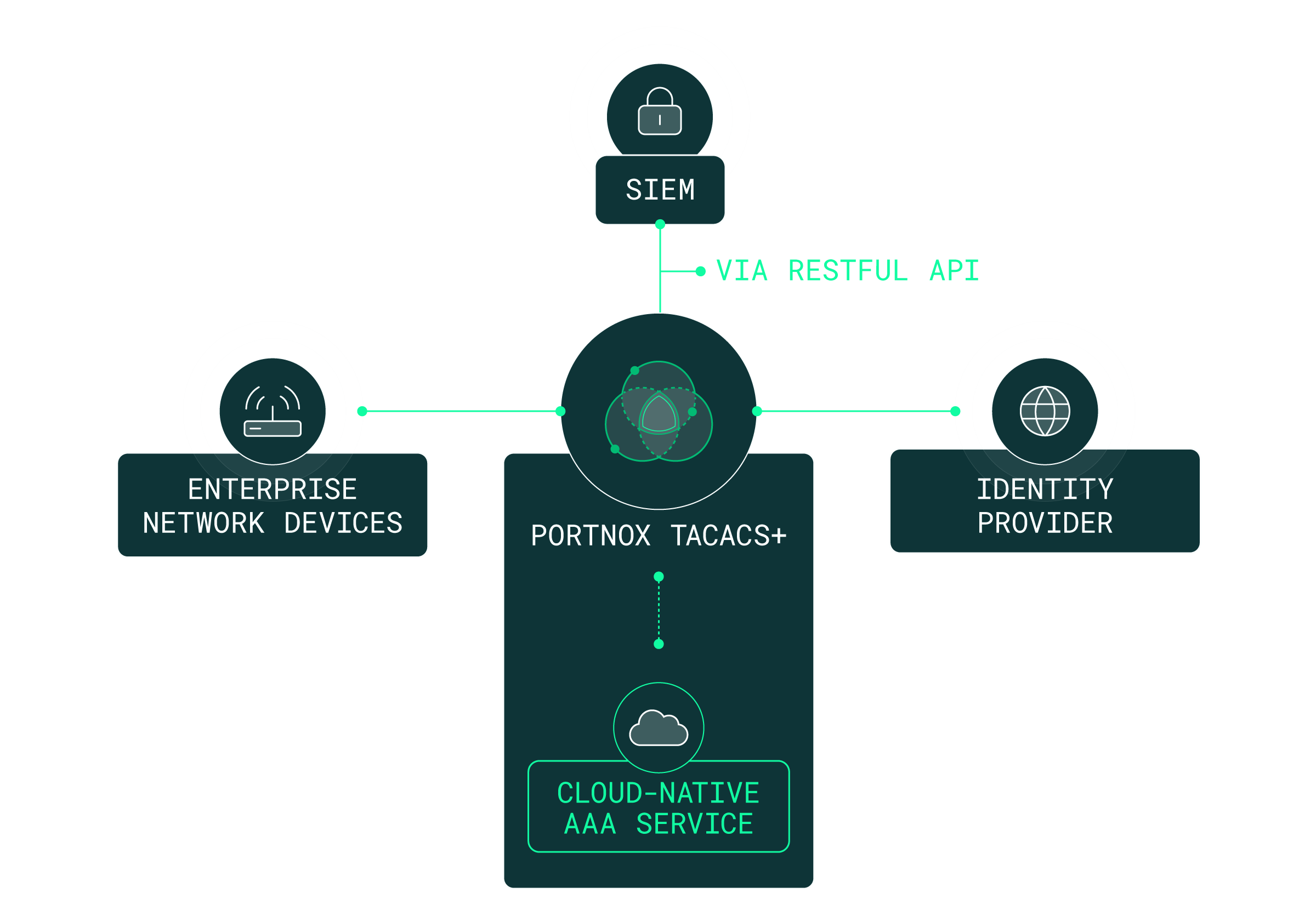
Portnox’s TACACS+ (Terminal Access Controller Access-Control System) provides a robust framework for managing and securing network devices by centralizing the authentication, authorization, and accounting processes.
Ensure that only authorized users from across your organization’s IT security team can access switches and wireless access points, and subsequently perform authorized actions on them.


NETWORK DEVICE ADMINISTRATION
Network device administration refers to controlling and securing administrative access to network infrastructure such as routers, switches, firewalls, and wireless controllers. With Portnox Cloud, network device administration is enforced using cloud-native TACACS+ to authenticate administrators, apply role-based permissions, and maintain detailed audit logs—ensuring only authorized users can make configuration changes to critical infrastructure.
Portnox Cloud secures network device administration by centralizing authentication and authorization through a cloud-delivered TACACS+ service. Administrator access is verified using identity-based policies, role-based access controls, and least-privilege enforcement. This eliminates shared credentials, reduces misconfiguration risk, and provides full visibility into who accessed which devices and what actions were performed.
Network device administration is a core component of zero trust because infrastructure access represents one of the highest-impact attack surfaces. Portnox Cloud applies zero trust principles by requiring continuous verification of administrator identity and enforcing granular access controls. No administrator is implicitly trusted, and access can be tightly scoped, monitored, and audited across all network devices.
Yes, Portnox Cloud can replace traditional on-prem TACACS+ servers with a fully cloud-native alternative. Organizations gain centralized network device administration without maintaining hardware, managing upgrades, or dealing with availability issues. Portnox Cloud simplifies deployment, improves scalability, and ensures consistent policy enforcement across distributed environments without increasing operational overhead.
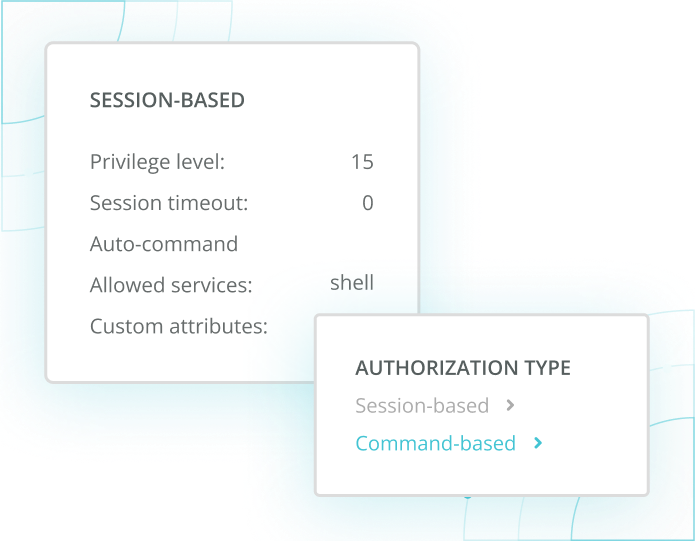
Portnox Cloud supports role-based network device administration by assigning administrators specific privileges based on their job function. Using TACACS+, Portnox enforces command-level authorization, ensuring users can only execute approved actions on network devices. This minimizes human error, reduces insider risk, and aligns administrative access with security best practices.
Yes, Portnox Cloud provides detailed auditing and logging for all network device administration activity. Every authentication attempt, authorization decision, and administrative action is recorded centrally. This enables organizations to meet compliance requirements, investigate incidents quickly, and maintain accountability across all network infrastructure access—without relying on fragmented or device-level logs.
Portnox Cloud is designed to scale network device administration across multi-site and globally distributed environments. As a cloud-native solution, it enables centralized policy management and consistent enforcement everywhere. Organizations can securely administer network devices across campuses, branches, and data centers without deploying additional infrastructure or managing location-specific TACACS+ servers.
Zero trust isn’t finished until access control is unified.
Portnox Cloud replaces legacy NAC, VPNs, and fragmented access tools with one cloud-native platform. No blind spots. No implicit trust. Just continuous, policy-driven access control—everywhere it matters.
Cloud-delivered administrative access control providing centralized authentication, authorization, and command auditing for all network infrastructure.
Modern, cloud-based NAC securing wired and wireless access with instant device discovery, posture validation, and automated enforcement.
After completing the form, an email will be sent to you with the report download link.