So, picture this: a bunch of cybersecurity gurus got together and were like, “We need some rock-solid guidelines to keep our systems safe!” That’s how the CIS Controls were born…well, kinda. Now, NAC (Network Access Control) steps in to help enforce those security guidelines, ensuring only legit users and devices get access – like a bouncer for your network, keeping the bad guys out and the good guys free to work.

NAC can help in identifying and controlling hardware assets by enforcing authentication and authorization mechanisms before allowing network access. This is precisely what the Portnox Cloud enables – all without actually having to install or maintain any additional hardware on-site.
Portnox’s zero trust platform contributes to data protection efforts by ensuring that only authorized devices and users can access sensitive data stored on the network. The platform’s powerful network segmentation capabilities add security layers across the network for all users.
Network access control is designed to enforce access controls based on user roles, device types, or other criteria, ensuring that individuals or devices only have access to the resources necessary for their job functions. This functionality is available with with Portnox out-of-the-box.
Portnox seamlessly delivers network authentication and access control capabilities for all access layers, including wireless – no matter if designated for employees, guests or contractors. The platform can be layered over any wireless networking gear without any reconfiguration needed.
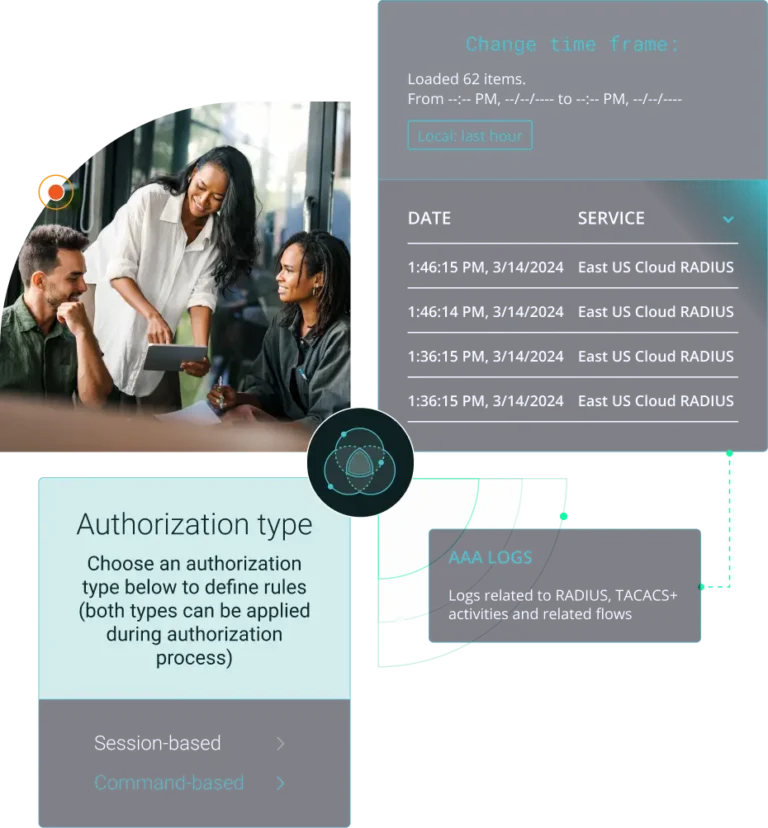
Not everyone on your IT team should be able to make changes to networking gear. With TACACS+ from Portnox, keep a tight grip on authentication, authorization, and accounting (AAA) policies for networking infrastructure without having to break the bank. Oh, and did we mention it’s fully cloud-native? Ditch the extra hardware and give our network device administration capabilities a go today.
CIS Controls
The CIS (Center for Internet Security) Top 20 Critical Security Controls, also known as the CIS Controls, provide a framework for organizations to establish a baseline of cybersecurity practices. These controls are designed to help organizations protect their systems and data from cyber threats. As of my knowledge cutoff in September 2021, the CIS Controls version 8.0 was the latest version available. The following is an overview of the CIS Top 20 Critical Security Controls:
Please note that the CIS Controls may be updated periodically, so it’s always a good idea to refer to the latest version of the CIS Controls for the most up-to-date information.
Yes, network segmentation is addressed in the CIS Controls. Specifically, Control 12 in the CIS Controls framework is titled “Boundary Defense” and encompasses measures related to network segmentation. The goal of this control is to prevent unauthorized network traffic and protect critical systems and data by implementing network segmentation.
Network segmentation involves dividing a network into smaller, isolated segments or subnetworks. This separation helps in containing and limiting the impact of a security breach or unauthorized access. By implementing network segmentation, an organization can create barriers and controls that restrict the lateral movement of attackers within the network.
Control 12 of the CIS Controls emphasizes the following actions related to network segmentation:
Network segmentation plays a crucial role in enhancing the overall security posture of an organization by limiting the attack surface, minimizing the potential impact of a security incident, and enabling more focused security monitoring and enforcement.
The CIS Controls framework does address endpoint compliance as part of its overall security recommendations. Several controls within the framework focus on ensuring that endpoints (such as desktops, laptops, servers, and mobile devices) are properly secured and compliant with security policies. Here are some of the controls that address endpoint compliance:
These controls, among others in the CIS framework, collectively contribute to establishing and maintaining endpoint compliance by addressing key areas such as inventory management, vulnerability management, secure configurations, user access controls, and malware protection. By implementing and adhering to these controls, organizations can enhance the security and compliance of their endpoint environments.
The CIS Controls framework provides guidance on suggested measures for risk remediation to help organizations address and mitigate security risks effectively. The controls offer recommendations and best practices to remediate vulnerabilities and improve overall security posture. While the specific measures may vary depending on the organization’s context, here are some general suggested measures for risk remediation outlined by the CIS Controls:
These suggested measures for risk remediation, combined with other controls in the CIS Controls framework, help organizations establish a proactive approach to cybersecurity, improve their security posture, and mitigate risks effectively. It is important to adapt these measures to the specific needs and risk landscape of each organization.
After completing the form, an email will be sent to you with the report download link.