Technical Sales / Presales at Routelink Integrated System
Security shouldn’t slow your business down. Portnox delivers universal zero trust that reduces breach risk by 75% and delivers 287% ROI. No passwords. No compromise.
SECURING THOUSANDS OF ENTERPRISES & MILLIONS OF DEVICES WORLDWIDE
Remove passwords entirely—no credentials to steal, phish, or reuse. Passwordless authentication eliminates the #1 attack vector in the vast majority of breaches, making compromise impossible for attackers. What can’t be stolen can’t be breached.
Connect users and devices to what they need—fast, frictionless, secure. Access works across network, SaaS, and on-prem without bottlenecks or complex configurations. Security that enables business velocity, not blocks it.
Enforce policy automatically—for users, devices, AI and more. Every access decision is continuously verified based on identity, context, and risk. When conditions change, access adapts instantly. Zero trust that actually works at enterprise scale.
Business Impact
How does passwordless zero trust perform at enterprise scale? Forrester’s composite analysis of six deployments provides the peer-validated benchmark your CFO is asking for.
The Total Economic Impact(TM) Of Portnox Cloud, a commissioned study conducted by Forrester Consulting, December 2025.Results are based on a composite organization representative of interviewed customers.

Our Platform
Block unauthorized devices—BYOD, IoT / OT, unmanaged—before they connect with cloud-native NAC from Portnox. Enforce zero trust compliance automatically at every access layer and stop threats at the edge.
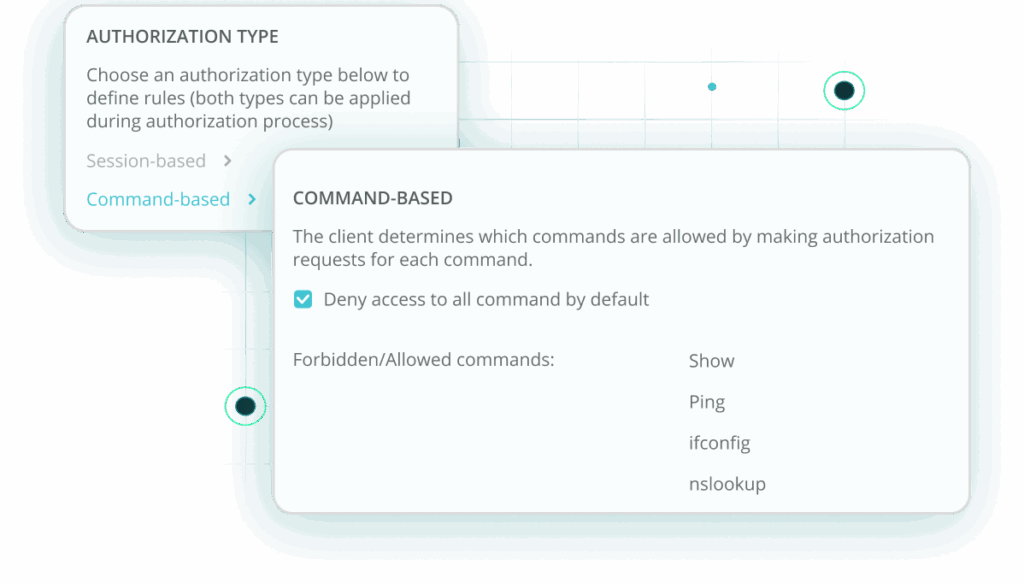
Grant least-privilege access to applications—not entire networks—with Portnox ZTNA. Users and devices connect only to authorized resources, regardless of location, with continuously verified trust.
Control and audit privileged access to network infrastructure with TACACS+ from Portnox. Authenticate, authorize, and log every administrator action on switches, routers, and critical systems.
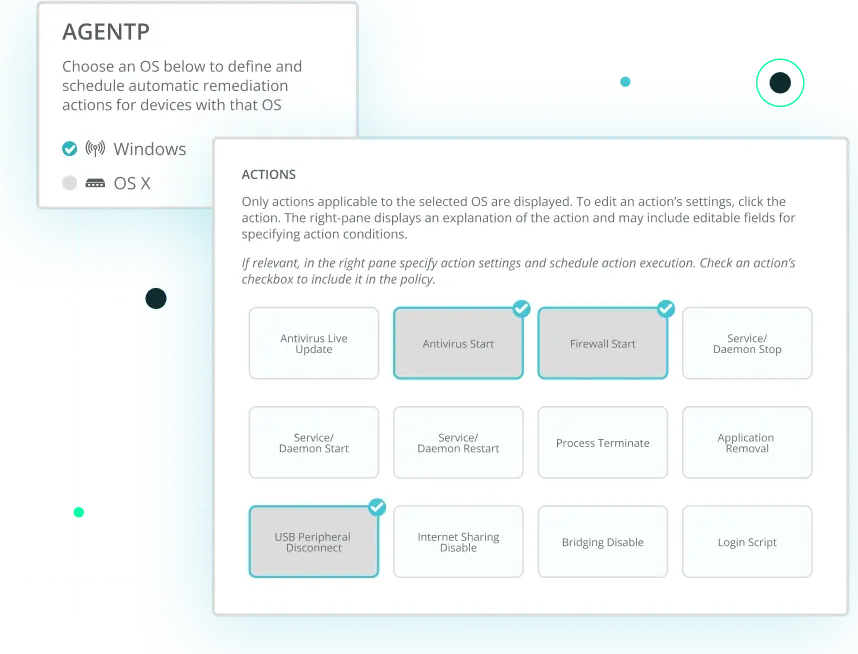
Take control of every connection to your network with a cloud-native, passwordless-capable NAC built for today’s hybrid, device-dense environments. Portnox automatically discovers, profiles, and monitors every managed and unmanaged device the moment it attempts to connect—without on-prem appliances or complex configurations.
Enforce security policies consistently across wired, wireless, and VPN access using strong, identity-based and certificate-backed authentication instead of shared passwords. With Portnox, you gain real-time visibility, automated enforcement, and the ability to scale secure, passwordless access control globally—without the operational drag of legacy NAC.
Give remote and mobile workers seamless, passwordless access to the resources they need—without the friction or overhead of a traditional VPN. Portnox delivers modern, agentless access to internal and cloud applications, dynamically verifying user identity, device posture, and risk before granting entry.
Fine-grained application access control reduces attack surface by ensuring users see only what they’re authorized to access. With a cloud-native architecture that eliminates bottlenecks and complexity, Portnox enables secure, passwordless productivity while keeping sensitive systems fully protected.

Bring your infrastructure administration into the cloud era with a modern TACACS+ solution that eliminates hardware, reduces overhead, and delivers granular visibility into every privileged action. Centralize authentication, authorization, and accounting (AAA) for all network and security devices to ensure consistent, policy-driven control over your critical infrastructure.
Portnox provides detailed session logging, real-time oversight, and automated enforcement that prevents unauthorized changes or risky configurations. By consolidating admin access into a single, cloud-native platform, you close security gaps and give your teams a simpler, more secure way to manage your environment.

Reduce exposure with a continuously adaptive approach to endpoint and user risk. Portnox evaluates device posture, user behavior, and contextual signals around the clock to determine whether access should be allowed, limited, or revoked entirely. When risk levels change, policies adjust instantly—isolating devices, triggering segmentation, or blocking access without human intervention.
The result is automated risk response that keeps attacks contained, minimizes dwell time, and strengthens your overall security posture without burdening your IT or security teams.

Meet compliance mandates with confidence through comprehensive, audit-ready visibility into every device and connection across your organization. Portnox centralizes access activity, posture data, and enforcement actions so you can easily demonstrate adherence to internal policies and external regulatory frameworks.
Streamline guest and contractor access with secure, policy-aligned onboarding flows that prevent unmanaged devices from becoming blind spots. With built-in, automated enforcement, you ensure that every connection meets your requirements—reducing audit headaches and eliminating manual oversight.

Portnox Delivers
Portnox delivers the scale, reliability, and global infrastructure that Fortune 2000 companies depend on—with the speed and simplicity that modern IT teams demand.
99.999% Uptime
Resilient by design. Multi-region cloud architecture with automated failover—without downtime, without disruption.
Continuously Validated
Third-party penetration testing, active bug bounty programs, and SOC 2 Type II compliance. Security without blind spots, without assumptions, without excuses.
US, EU, and APAC
Global infrastructure delivers low latency worldwide. Fast, reliable access—without geographic barriers.
Operational in Days
No appliances. No infrastructure. No complexity. Deploy in days—not quarters. Scale to 100K devices without professional services.
The AI Access Control Gap
WORKS WITH YOUR STACK
Independent Validation
Forrester’s independent analysis of six enterprise deployments validated what eliminating password-based attacks and enforcing continuous zero trust delivers for the business.
ROI
Three-year return on investment
Month Payback
Time to positive cash flow
Net Value
Net present value over three years
“
”
Josh T.
“
”
“
”
“
”





After completing the form, an email will be sent to you with the report download link.