Why today’s boundless company networks are like castles without walls being protected by network security systems stuck in the middle ages.
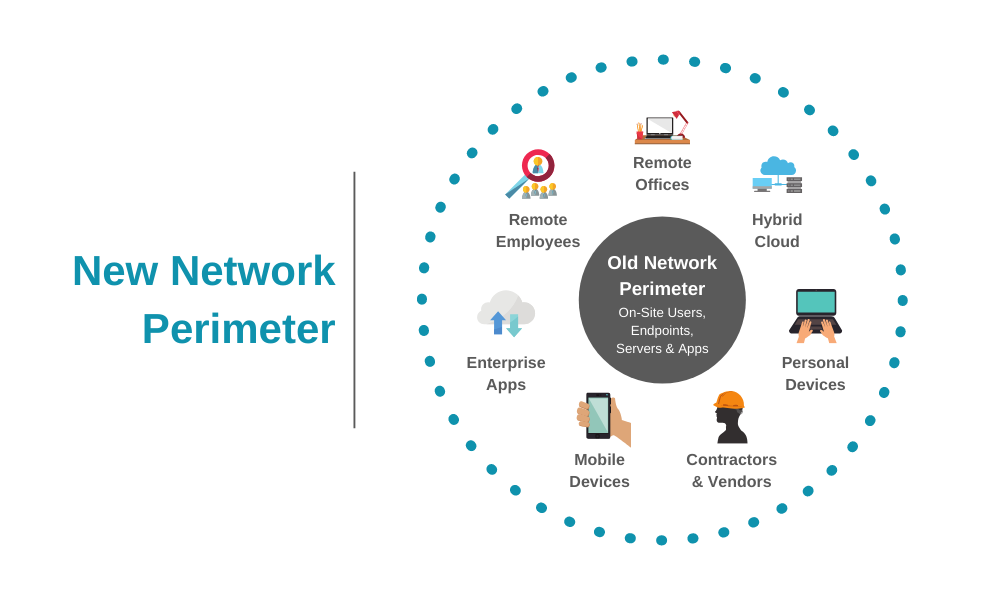
Today, your network is likely comprised of your LAN, MPLS, SD-WAN, employees’ homes, Azure, Starbucks, Marriott, any airport…you get the idea. Your network extends to wherever authorized devices connect to gain access to company resources.
All of this proprietary, confidential or merely sensitive data being accessed across these parts of the network is no longer safe behind your castle walls. Access to everything (from everywhere) has changed the security dynamic.
How does zero trust factor in?
Enter zero trust, a new – well, maybe not that new – but let’s say in vogue network security model that is focused to address the challenges posed by today’s increasingly complex and extended corporate networks.
The zero trust model does not require or expect you to have walls around your networks. With zero trust, as the name implies, NOTHING inside or outside a company is trusted. That means no devices or systems used by employees is automatically trusted.
Traditional NAC meet zero trust requirements
Now, this security model may seem familiar. Isn’t this just like network access control (NAC)? Well, yes and no. NAC has been around since the early 2000s, and has been primarily focused on ensuring only valid and authorized devices can access your network. Traditionally, however, NAC solutions have only focused on the LAN, as that was what existed within the castle walls of an organization. But as I’ve stressed, the typical network extends far beyond the LAN today.
To truly achieve zero trust, organizations need a NAC solution that can easily and effectively work when your castle has no walls.
NAC for today’s sprawling networks
Since your employees are likely on the move and using several different devices (desktop, laptop, phone, etc.), any NAC would need to have device awareness no matter where the device is geo-locationally. And that means not only when it is joining the LAN, but also when it is connecting from home, from a remote office, from Starbucks – awareness anywhere and everywhere, always.
Perhaps the most critical factor when assessing your network security needs is having the ability to continuously monitor endpoint risk. After all, you can’t just go around authorizing every company PC to connect if it’s not “trusted.”
Ensuring endpoints are in a company compliant state, minimizing or eliminating the potential for endpoints to be hacked and used to bridge your network is crucial. This requires a NAC that is always aware of endpoint risk and can use that to allow or block access. Today, this mixture give your network the best chance of minimizing such threats.
It’s the control part of NAC that ultimately brings the most added value versus endpoint-only zero trust solutions. The ability to not only allow access to your trusted devices, but also to control that access by placing them on the proper VLAN or under an appropriate access control list (ACL) adds a powerful layer of security.
The answer is in the cloud
Lastly, a NAC for today’s boundless network must be “light weight.” You don’t want to be deploying appliances or software in every remote location, store or office. It takes an immense amount of bandwidth and expertise to properly execute. Can’t that investment be better spent elsewhere?
This is where traditional NAC solutions fall short. Since they were designed for the old castle network model, they simply aren’t equipped to give you the full visibility and control you need over your extended network to prevent breaches.
The answer is NAC delivered as a cloud service. Manageable from anywhere, coverage for everywhere, and with continuous device awareness – a cloud-delivered NAC adhering to the zero trust model can future-proof your increasingly extended network.
Try Portnox Cloud for Free Today
Gain access to all of Portnox's powerful zero trust access control free capabilities for 30 days!