Endpoint security is a fine line to walk—users will inevitably want to connect to the corporate network with a variety of devices set up according to their personal preferences. IT will want to maintain control over any device that joins the network, and make sure that the risk these outside devices pose is as low as possible. Thankfully there is a happy medium—endpoint risk monitoring and assessment with Portnox.

Users may prioritize ease-of-use over security, but IT has a responsibility to make sure personal devices don’t expose the organization to more threats. Having a passcode on a phone, making sure anti-virus software is up to date, and running a firewall are some basic measures that should not interfere with everyday functions, but how can IT make sure these policies are enforced? Well, Portnox’s endpoint risk assessment functionality can check all of those boxes…and more.
Portnox’s powerful risk assessment policy capabilities let you specify requirements across a variety of devices and operating systems – from the Windows firewall to peripherals on macOS and the passcodes on Android and iOS. That means your BYOD devices won’t be bringing you increased vulnerabilities. And risk policies are constantly evaluated, so no post-connection changes can sneak past the watchful eyes of Portnox.
Faced with rising costs and operational complexity from legacy NAC, AbsoluteCare transitioned to Portnox Cloud to support its HITRUST certification goals and growing healthcare environment. In this case study, see how a cloud-native NAC approach eliminated on-prem infrastructure, simplified deployment, and enabled real-time endpoint risk monitoring—delivering stronger security with far less effort.

ENDPOINT RISK MONITORING
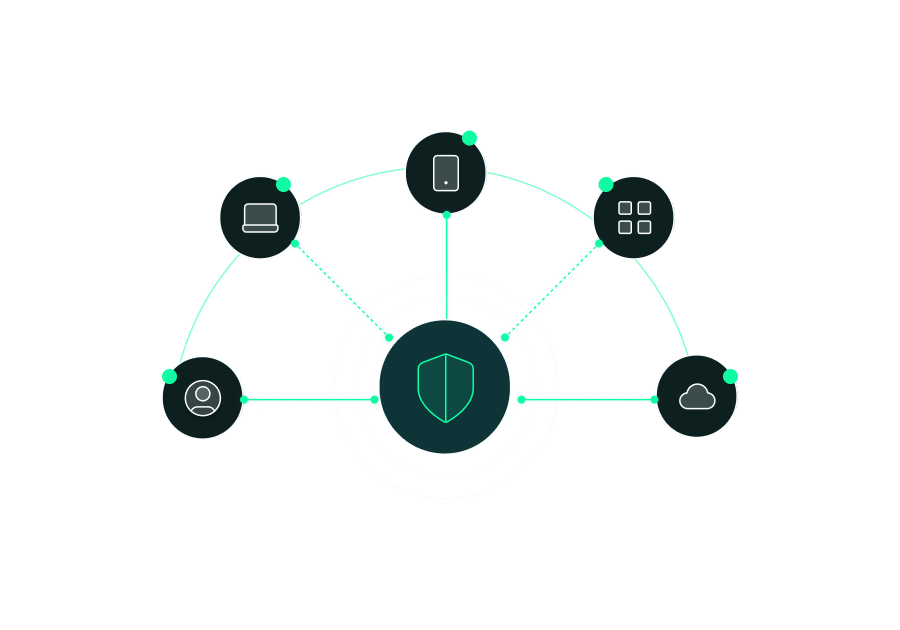
Endpoint risk refers to the security exposure created by devices connecting to enterprise networks and applications. This includes unmanaged devices, outdated operating systems, missing patches, weak configurations, or suspicious behavior. Portnox Cloud continuously evaluates endpoint risk by monitoring device posture and compliance, helping organizations prevent vulnerable endpoints from accessing sensitive resources before they become an attack vector.
Portnox Cloud identifies endpoint risk by continuously assessing device posture across wired, wireless, and remote environments. It evaluates factors such as operating system health, security configuration, certificate status, and compliance with policy. By correlating these signals in real time, Portnox determines whether an endpoint poses risk and automatically enforces access controls based on that assessment.
Endpoint risk monitoring is essential to zero trust because access decisions should never rely on identity alone. Portnox Cloud incorporates endpoint risk into every access request, ensuring that only healthy, compliant devices are allowed to connect. If endpoint risk changes—due to misconfiguration or policy violation—access can be restricted or revoked automatically, enforcing continuous zero trust verification.
When endpoint risk increases, Portnox Cloud can automatically enforce corrective actions based on policy. This includes restricting access, quarantining the device, redirecting users to remediation workflows, or blocking access entirely. These automated responses reduce reliance on manual intervention and help contain risk quickly—before vulnerable endpoints can impact network or application security.
Yes, Portnox Cloud monitors endpoint risk both on and off the network. Using lightweight agents and cloud-based policy evaluation, Portnox maintains visibility into device posture regardless of location. This ensures endpoint risk is consistently assessed for remote, hybrid, and on-site users—closing gaps that traditional network-only security controls often miss.
Endpoint risk monitoring reduces attack surface by preventing non-compliant or high-risk devices from accessing enterprise resources. Portnox Cloud ensures only endpoints that meet security standards are granted access, limiting exposure from BYOD, contractor devices, and unmanaged endpoints. By enforcing least-privilege access based on real-time risk, organizations significantly reduce lateral movement opportunities.
Portnox Cloud simplifies endpoint risk management by automating posture assessment, policy enforcement, and remediation actions. IT teams gain centralized visibility into endpoint risk without deploying complex infrastructure or managing manual workflows. With cloud-native deployment and real-time enforcement, Portnox reduces operational burden while strengthening security across users, devices, and access points.
You’ve embraced zero trust—now enforce it everywhere.
Portnox Cloud unifies access control across your environment in a single, cloud-native platform. Fewer tools. Fewer gaps. Smarter security by design.
Cloud-delivered administrative access control providing centralized authentication, authorization, and command auditing for all network infrastructure.
Modern, cloud-based NAC securing wired and wireless access with instant device discovery, posture validation, and automated enforcement.
After completing the form, an email will be sent to you with the report download link.