Cyber Security Essential #2: 802.1x Network Access Control
Why is 802.1x Network Access Control Essential?
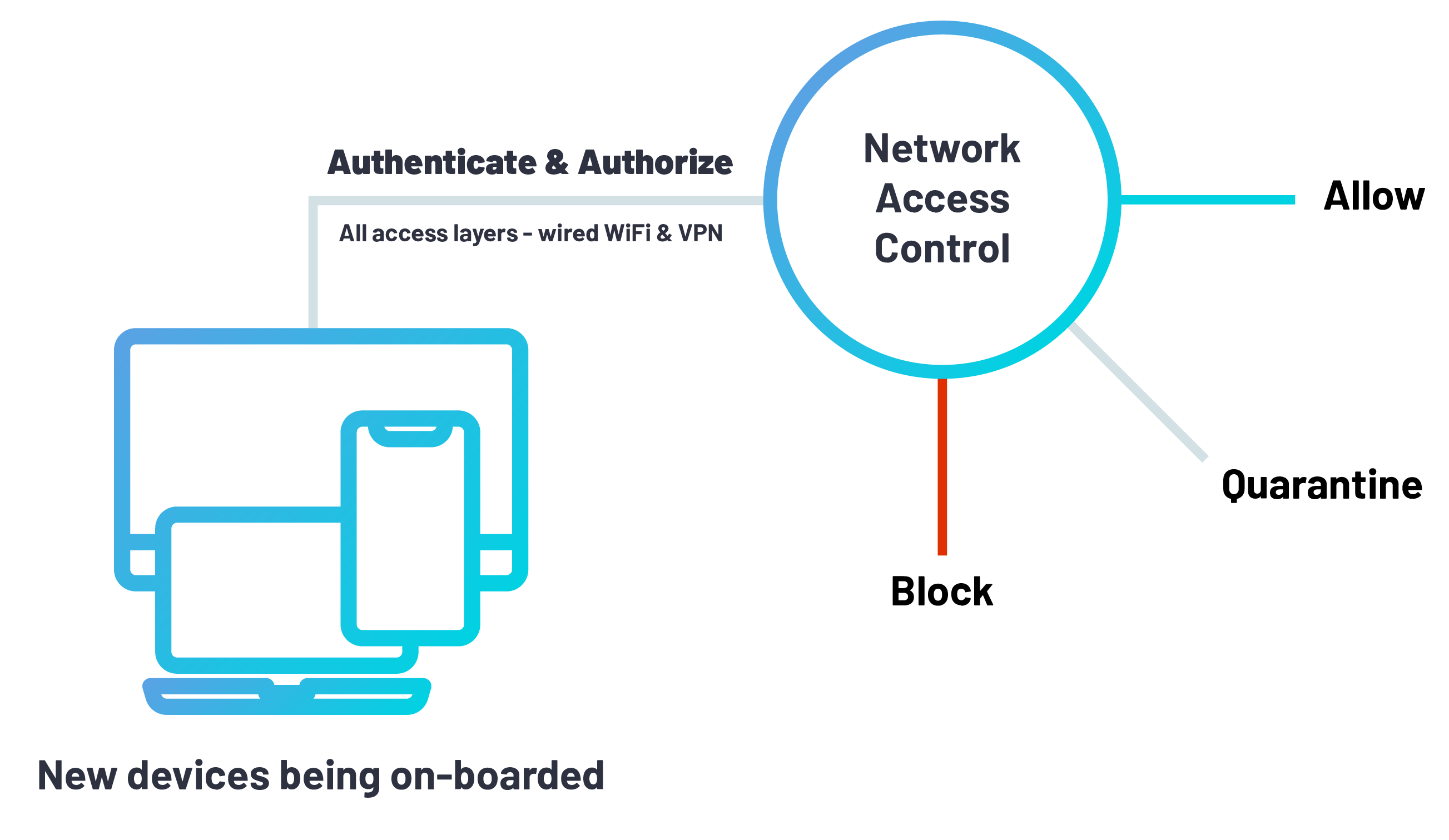
802.1x network access control is a technology that enables organizations to enact its own unique policy for how and when endpoints (desktops, laptops, smartphones, etc.) can connect to their corporate networks. NAC solutions are typically designed to allow IT security teams to gain visibility of each device trying to access its network, and specifically the type of device and access layer being used (i.e. wifi, wired ports, or VPN).
Today, 802.1x network access control provides a number of powerful features on top of what it was originally designed for years ago. These include security posture assessments for endpoints, which pinpoints any associated endpoint risks, allowing network security administrators to control network access based on their organization’s risk tolerance threshold.
With the rise of cloud computing, remote workforces, bring-your-own-device (BYOD) policies, and the internet of things (IoT), network access control has become a much more critical part of the larger cybersecurity technology stack at most companies. The technology itself has also evolved quite drastically in response to these emerging trends and their impact on networking and ensuring network security.
Key Functionality to Consider When Deploying a NAC Solution
Network Visibility & Device Discovery
A NAC solution discovers and identifies all devices/users in the network before they are granted network access, requiring continuous monitoring of the network and devices connected to it. The system enables the discovery, classification and assessment of every device connected to the network. Configuration and security state of every device is monitored, ensuring that the network and devices are compliant to the organizational security policy.
Full Access Layer Coverage
As today’s networks explode in size and scope, particularly with remote workforces on the rise, it’s imperative that your 802.1x network access control solution can manage access control across all existing access layers. This includes the obvious – wired ports and WiFi. It also must be able to manage the various remote access methods used within your organization. These may include VPN, Teleworker Gateways, and beyond.
Authentication Services
Traditionally, enterprises have enabled network authentication via usernames and passwords. As we now know today, this method of authentication can be easily compromised by bad actors, making it no longer sufficiently secure for enforcing network access control. Any NAC worth its salt should offer several methods for authentication, including: role-based, MAC authentication bypass (MAB), and certificate authority.
Device On-Boarding
Business units and even departments (think Finance & Accounting, for example) often have their own VLANs since they’re dealing with very sensitive, confidential data. The task of setting up such VLANs and onboarding new devices is just one of dozens of tasks overseen by frequently overburdened IT teams. So, if not done correctly at first, it can open the door to potential network vulnerabilities, such as a person gaining access to a part of the network he/she should not have the privileges for. At a small scale, managing access manually is often sufficient. For larger organizations, however, this just isn’t sustainable. As a result, many large organizations that don’t have a secure onboarding process will often compromise on network security hygiene.
Policy Configuration
Network security teams define and activate access control policies to control device access to the corporate network, which is ultimately based on the device authorization state. Once a device is authorized for network access, a network access policy determines which specific virtual LAN (VLAN) that device or user is directed to. On top of that, the policy also defines, for each type of authorization violation, whether to deny entry or whether to quarantine the device by assigning it to a specific VLAN or apply an access control list (ACL).
Endpoint Risk Monitoring
Your corporate network is only as strong as its weakest security link. This means continuous risk posture assessment is paramount. By continually monitoring the network, your network and security teams can stay ahead of cyberattacks with the ability to identify new risks in real-time, react to these risks, and take action. In a world with ever-expanding boundaries and an exponential increase in types of endpoints, continuous risk posture assessment must function no matter location, device type, or the type of data being transferred.
Device Remediation
Having a rapid remediation plan in place will not only help prevent further damage or the lateral spread of attacks but also allow for business continuity. Effective endpoint remediation consists of:
- Automated Patch Updates Across the Network – Enforce necessary patch, anti-virus, operating system, and application updates across managed and unmanaged endpoints.
- Immediate Incident Response – Contain ransomware events by remotely disconnecting endpoints from the network without the need for manual intervention.
- Armed Incident Response Teams – Arm IT professionals and network admins with the ability to remotely take actions on employees’ devices. The proliferation of IoT devices over the last decade has prompted a growing number of network security concerns. With all of these devices – printers, CCTV cameras, ATMs, MRI machines, etc. – now connected to their respective networks, it’s exponentially expanding corporate threat surfaces.
Compliance Enforcement
NAC is used to enforce regulatory policies and maintain compliance across the organization. In practice, this typically means:
- Understanding how mobile, BYOD, and IoT devices will affect and transform not only the organization but the industry and implementing the right processes and tools control them.
- Tracking any network related device or program in real-time via a centrally secured platform providing full and actionable visibility.
- Controlling access to the network and to cloud applications, even based on the geographical locations of users.
- Ensuring that the business is in compliance with governmental regulations like SOX, PCI DSS, HIPPA, FINRA, FISMA, GLBA among others. Strict compliance will provide legitimacy with clients and partners.
Try Portnox Cloud for Free Today
Gain access to all of Portnox's powerful zero trust access control free capabilities for 30 days!