The Firewall is Here to Stay
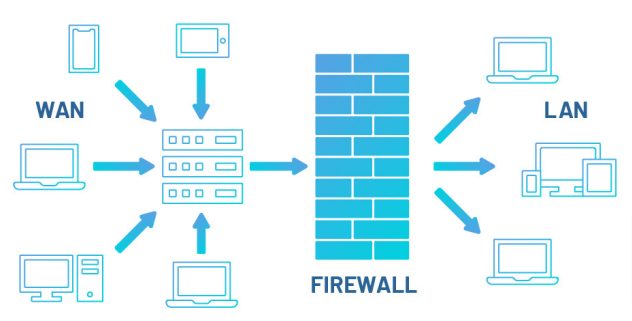
A firewall is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules. Firewalls have been a first line of defense in network security for decades. They establish a barrier between secured and controlled internal networks that can be trusted and untrusted outside networks, such as the Internet.
Firewalls have evolved beyond simple packet filtering and stateful inspection. Most companies are deploying next-generation firewalls to block modern threats such as advanced malware and application-layer attacks. Next-generation firewalls (NGFW) are more sophisticated than packet-filtering and stateful inspection firewalls. Why? They have more levels of security, going beyond standard packet-filtering to inspect a packet in its entirety. That means inspecting not just the packet header, but also a packet’s contents and source. NGFW are able to block more sophisticated and evolving security threats like advanced malware.
Necessary Capabilities
Advanced Threat Protection
Most traditional firewalls integrate with a separate intrusion prevention system (IPS) to gain additional security features. Next generation firewalls have IPS capabilities built in to protect against a wide variety of threats, such as DDoS attacks, malware and spyware. Further integration with threat intelligence systems like SIEM provide advanced layers of protection to defend against the modern threat landscape.
SSL Inspection
Malicious threats can be hidden within encrypted web traffic. In order to filter out malicious content, the NGFW intercepts encrypted web activity to filter out malicious activity through a “man in the middle” approach. The NGFW will first decrypt the incoming web traffic and then scan for threats like malware or viruses. After its examination, the traffic will be encrypted and forwarded to the user so that the user can access the data as originally intended.
Application Control
The users on your network use several tools on their devices, such as email, social media and other vendor applications. Some of these web applications can be malicious and lead to open backdoors that can be exploited to enter your network. Application control allows organizations to create policies that either allow, deny or restrict access to applications. This not only protects organizations by blocking risky applications but also helps them manage their application traffic to ensure availability for business-critical resources.
User Identity Awareness
User identity awareness allows organizations to enforce policies that govern access to applications and other online resources to specific groups or individuals. The NGFW integrates with your authentication protocols (such as LDAP or Active Directory) so that access is governed by user identity as opposed to IP address. User identity awareness not only helps organizations control the types of traffic allowed to enter and exit their network but also manage their users.
Deep Packet Inspection
Deep packet inspection inspects data to identify and filter out malware and unwanted traffic. By inspecting the content of a data packet, the NGFW can intelligently determine which applications are being used or the type of data being transmitted. This allows the firewall to block advanced network threats (such as DDoS attacks, trojans, spyware and SQL injections) and evasion techniques used by threat actors.
Centralized Management
Firewalls need proper security management to ensure that they meet the security needs of the organizations that need protection. Firewall capabilities need to be updated and firewall rules need to ensure they are being properly enforced. Centralized management of your firewall(s) is crucial in gaining on overall view of your firewall configurations. Organizations need to ensure they can scale their firewall to ensure that their organization has maximum protection to fit their growth needs.
Reporting & Insights
Firewalls generate logs that detail information about security and network traffic that security administrators review to understand the overall activity. This information provides organizations with useful insights to help them prioritize application traffic and understand their network security and monitor user activity.
Try Portnox Cloud for Free Today
Gain access to all of Portnox's powerful zero trust access control free capabilities for 30 days!