Today, Chief Information Security Officers (CISOs) are faced with the daunting task of minimizing risks, optimizing budgets, and ensuring compliance with industry standards such as the CIS Controls V8. One powerful tool in the CISO’s arsenal for achieving these goals is Network Access Control (NAC). By leveraging NAC effectively, CISOs can enhance their organization’s security posture and streamline compliance with the CIS Controls V8.
Understanding the CIS Controls V8 and Their Importance
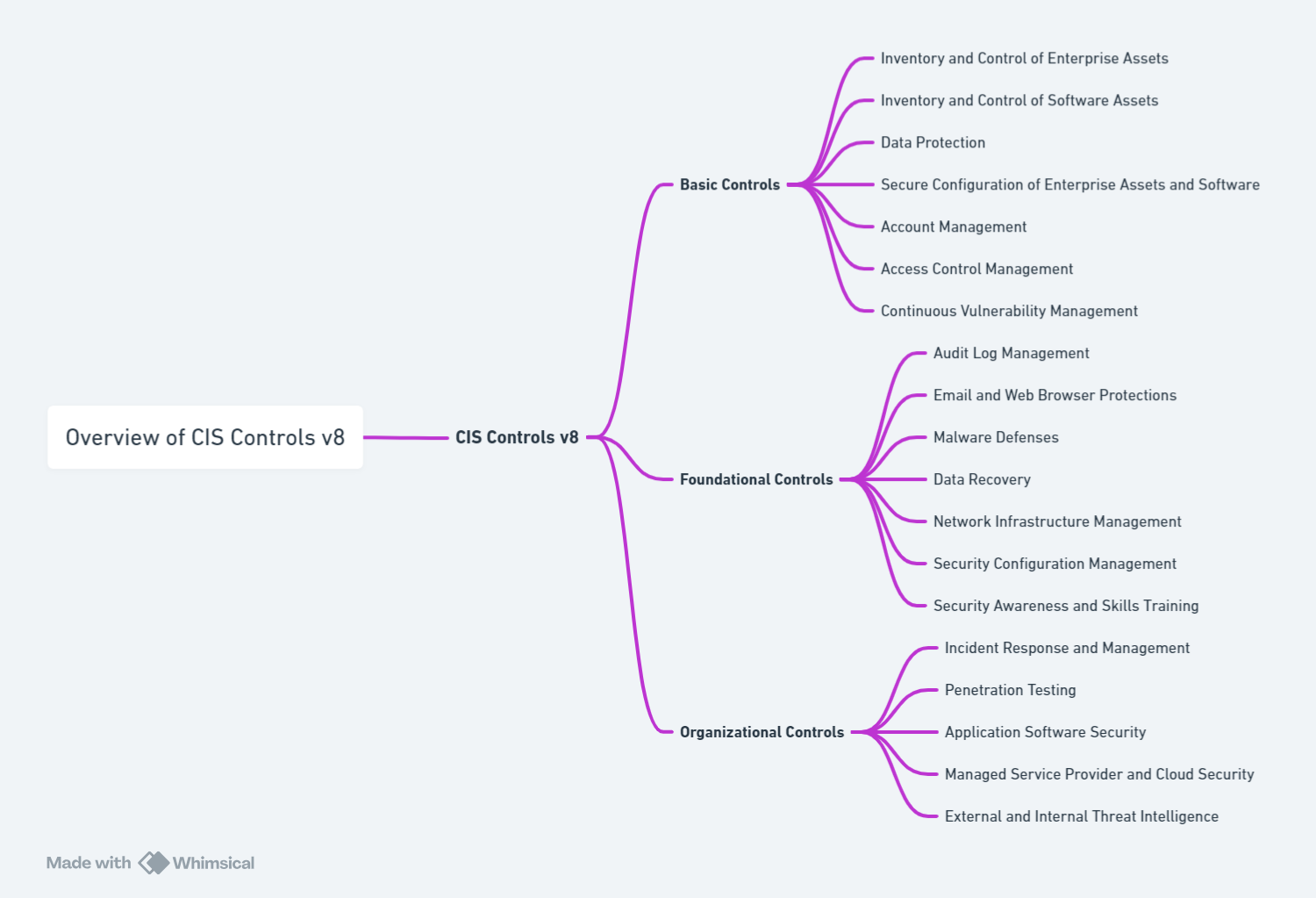
Navigating the complexities of the digital frontier, the CIS Controls V8 stands as a beacon for organizations aiming to fortify their defenses against the relentless wave of cyber threats. Crafted by the Center for Internet Security, these controls serve not merely as suggestions but as a meticulously structured blueprint guiding entities through the cybersecurity maze. Embracing the CIS Controls V8 is akin to equipping oneself with a strategic map, pinpointing vulnerabilities and directing efforts towards the most impactful defensive measures. It’s about understanding that in the vast expanse of potential security actions, prioritization is key. For organizations, this means adopting a focused approach to cybersecurity, one that channels resources into initiatives that promise the most significant reduction in risk. Through adherence to these controls, not only do organizations strengthen their shield against cyber-attacks, but they also navigate the complex regulatory landscape with greater ease, ensuring they meet industry standards and avoid the pitfalls of non-compliance. In essence, the CIS Controls V8 is less about ticking off a checklist and more about embracing a strategic framework that aligns with the overarching goal of creating a robust and resilient cybersecurity infrastructure.
The Role of Network Access Control in Modern Cybersecurity
Network Access Control (NAC) emerges as a cornerstone in the edifice of modern cybersecurity, orchestrating the harmonious interplay between access permissions and the sanctity of network environments. At its core, NAC is the gatekeeper, ensuring that only authenticated and authorized users and devices gain entrance to the network’s critical resources. Through mechanisms such as 802.1x authentication, NAC solutions extend their influence beyond mere access, weaving a tapestry of security that blankets the entire network infrastructure. This pivotal role of NAC in cybersecurity transcends conventional boundaries, empowering CISOs to sculpt a resilient and adaptive security posture. As the digital realm burgeons, teeming with both innovation and menace, the strategic implementation of NAC stands as a testament to an organization’s commitment to safeguarding its digital assets against the incessant tides of cyber threats. It’s in this context that NAC not only asserts its relevance but champions the cause of robust cybersecurity practices, making it an indispensable ally in the quest for a fortified digital domain.
Aligning NAC Features with CIS Controls V8 for Enhanced Security
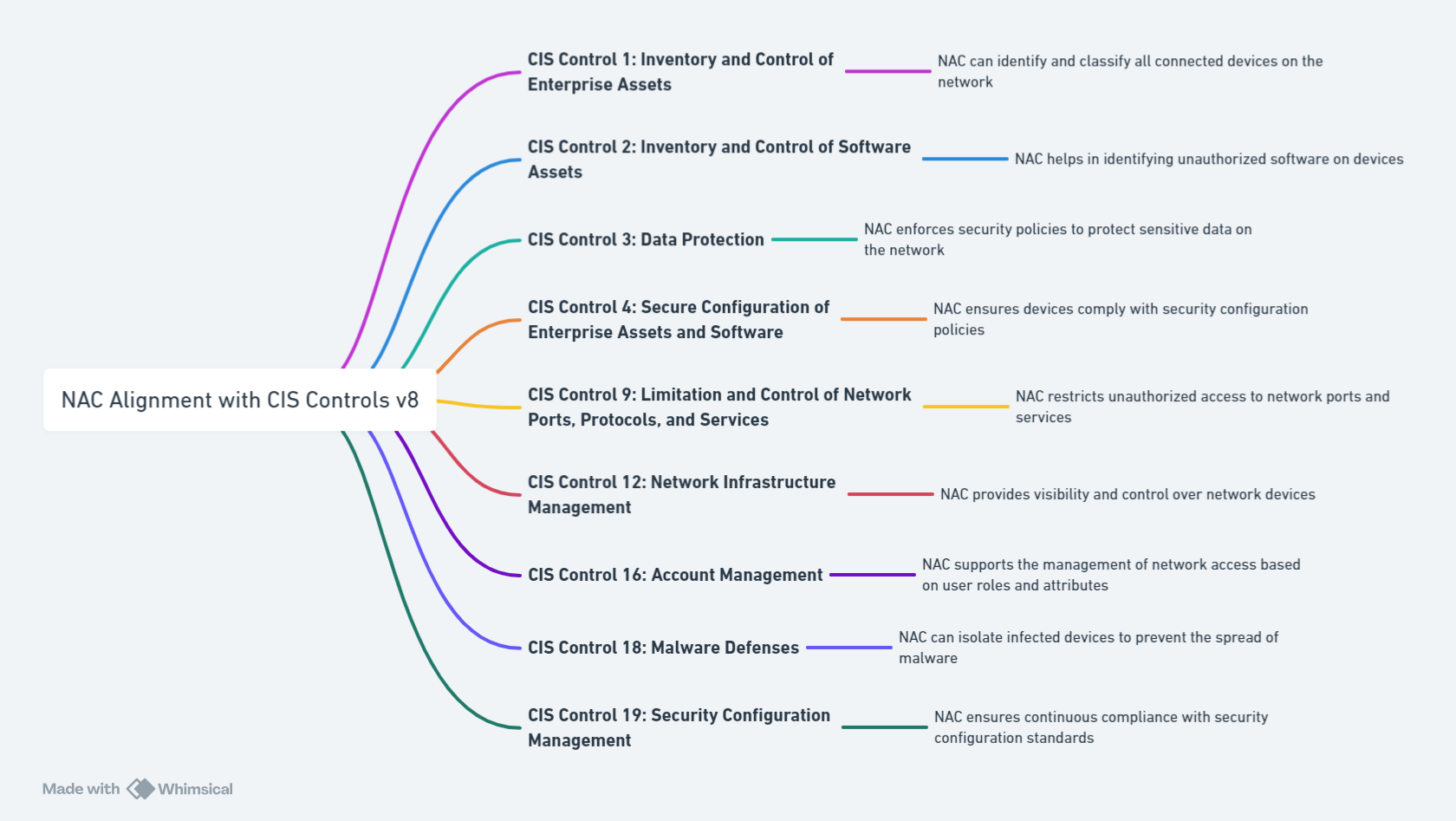
The strategic alignment of Network Access Control (NAC) features with the stipulations of CIS Controls V8 serves as a linchpin in bolstering organizational security frameworks. NAC’s robust capabilities offer a multifaceted approach to compliance, covering a spectrum from enforcing stringent access control policies to the vigilant monitoring of network activities. It meticulously checks for and intercepts unauthorized devices attempting to infiltrate the network, ensuring that only verified users and equipment can navigate through the digital ecosystem. This congruence between NAC functionalities and CIS Controls V8’s directives creates a fortified barrier against potential breaches, dramatically elevating the organization’s security posture. By embedding NAC at the heart of cybersecurity strategies, CISOs unlock a proactive defense mechanism, intricately designed to anticipate, thwart, and mitigate the gamut of cyber threats. It is this precise integration of NAC’s defensive arsenal with the proactive ethos of CIS Controls V8 that embodies the epitome of enhanced security, steering organizations towards a more secure and compliant future in the cyber realm.
Prioritizing Cybersecurity Investments with NAC for CIS Compliance
Navigating the intricate web of cybersecurity investments requires a discerning eye and a strategic mindset. Within this complex equation, Network Access Control (NAC) solutions represent a crucial variable, offering a powerful means to align with the principles of CIS Controls V8. For a CISO, the decision to allocate resources toward NAC is not merely a budgetary consideration but a strategic move towards fortifying the organization’s digital bastions. By incorporating NAC into the cybersecurity infrastructure, an organization not only tightens its access controls but also elevates its compliance posture. This dual advantage ensures that the investment extends beyond mere regulatory adherence, morphing into a robust defense mechanism against the ever-evolving threat landscape. Such strategic deployment of NAC can illuminate the path for resource optimization, ensuring that each dollar spent is a step toward a more secure and resilient digital environment. As the digital realm continues to expand, and threats become more sophisticated, prioritizing NAC for CIS Controls V8 compliance is not just prudent; it’s indispensable for those aiming to navigate the cybersecurity seas with confidence and efficacy.
Automating Compliance and Threat Response with NAC
In the dynamic theater of cybersecurity, automation stands as a beacon of efficiency, transforming how organizations adapt and respond to an ever-changing threat landscape. Network Access Control (NAC) emerges as a pivotal force in this automated revolution, offering tools that not only streamline compliance but also supercharge threat response mechanisms. With NAC, the arduous tasks of continuously monitoring compliance status and initiating immediate action against detected threats are elegantly automated. This automation is more than a mere convenience; it’s a strategic enhancement that amplifies the ability of organizations to maintain a vigilant stance against intrusions, all the while adhering to the rigorous demands of CIS Controls V8.
By harnessing the power of NAC’s automation capabilities, security processes that once consumed precious time and resources now operate with unparalleled efficiency. This shift not only accelerates the detection and neutralization of threats but also ensures a seamless compliance journey, where checks and balances occur in real-time, without the need for constant manual oversight. The end result is a cybersecurity framework that is not only more resilient and responsive but also one that thrives on the principles of proactive defense and compliance. Thus, in the quest for a robust cybersecurity posture, automating compliance and threat response with NAC emerges as a critical strategy, equipping organizations with the agility needed to outpace the cyber threats of tomorrow.
Related Reading
Try Portnox Cloud for Free Today
Gain access to all of Portnox's powerful zero trust access control free capabilities for 30 days!