Last Mile Security: Why It’s More Important Today Than Ever Before

It’s official: perimeter security is old news. Thanks to the rise of cloud services, SASE architecture, and global pandemics, it’s time we discussed securing the “last mile.” Last mile security is a lot like a marathon – it’s lonely and hard to get to – but without it, you won’t get a medal at the finish line.
What Constitutes the “Last Mile” Today?
The “last mile” refers to all of the network components that physically sit outside of your headquarters or branch offices, and that is used to connect to enterprise systems and resources by remote workers.
Typically, the initial line of demarcation beyond your organization is a router. These routers could be located within an employee’s home, at a local cafe (those places where we went to socialize prior to COVID-19…sigh), an airport, etc.
As you expand out beyond the router, you start to see an expanding network of unmanaged devices such as smart TVs, wireless phones, and smart home and home security appliances in residence. Last but not least – there’s the crown jewel – the employee’s primary endpoint – the device that he/she uses to access corporate resources and data remotely. Most of these network endpoints are out of your organization’s control, and it probably makes sense to leave it that way. It would be ideal, however, to be able to have visibility of the primary device connecting to the corporate network and cloud-based enterprise applications remotely (which we’ll cover in more detail below).
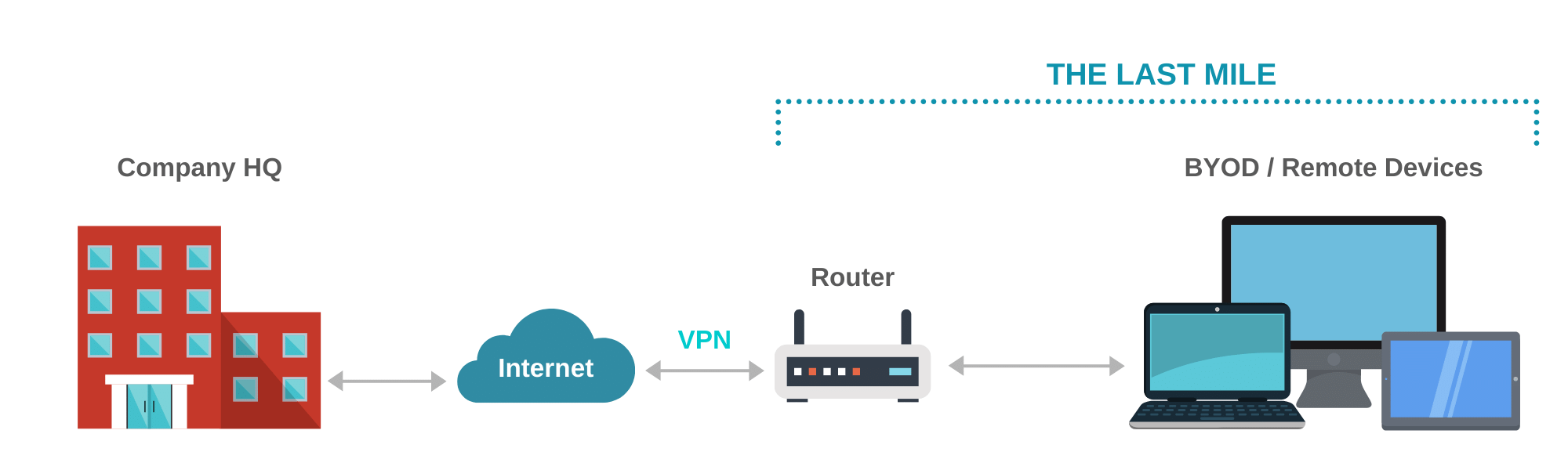
For the “cafe” or third-party public network, the same principle applies – they all contain untrustworthy devices, some of which are already vulnerable, some of which will be vulnerable in time, and some have likely been hacked already.
Last Mile Security Essentials
Ok, so we’ve set the stage for what the last mile landscape looks like today. Now it’s time to focus on how you can take steps to ensure that you’re securing the last mile and accounting for this seemingly endless list of remote access threats.
Let’s start with our champion – in this case, a personal (BYOD) or company-issued laptop running windows OS or MAC OSX. This device has access to enterprise cloud applications, and may even be able to access the corporate network remotely via VPN or VDI.
So, how can you institute effective last mile security in this instance? Well, there are a few basic requirements we must examine – a checklist if you will. The checklist looks at the protection of the endpoint, the identity of its user, and the prevention of common user mistakes. Let’s take a deeper dive…
I. Endpoint Posture Assessment
Generally speaking, to establish a clear and secure assessment of the champion endpoint’s posture, you must roll out:
- Firewall – so now you don’t have to worry about what’s going on beyond your perimeter.
- Anti-virus / Endpoint Detection & Response (EDR) – so if something goes beyond that first line of defense, you can block it or at least be alerted in order to mitigate.
- Up-to-Date Patches – so no one from the outside can bypass the first two by using known vulnerabilities.
In the last mile, continuous posture assessment must be enabled so threats can be discovered and managed in real-time before they become incidents. Why continuously? Because today your endpoint becomes part of the organization long before it connects through the VPN – it enters the sphere when it’s used to log into Salesforce, Office365, Box.com, or whatever cloud service that’s in use across the organization. Remember, these platforms all hold corporate data – some of which are particularly sensitive.
II. Risk Prevention
When employees don’t adhere to IT security best practices such as stopping the anti-virus or disabling the firewall, you not only want to know – in a perfect world you want to be to proactively prevent this from ever happening.
In another scenario, say an employee inserts a smartphone, all are acting as a USB disk – a notoriously risk-prone device – into their laptop, you want to be alerted and be able to disable it before it can cause harm to the endpoint or worse.
These actions sound small in the grand scheme of things, but they ultimately save time and lower organizational risk significantly.
III. Identity Protection
Using a strong password and updating it regularly doesn’t cut it anymore. Multi-factor authentication is now a mandatory requirement when it comes to safeguarding access to corporate assets, especially when accessing through the VPN.
Today, many people tend to hold onto things that seem to work well for as long as they can. So, using the same “P@ssw0rd” that only you thought of for your local grocery store rewards program, your primary bank account, and your VPN is probably the standard. The problem is, if anyone of those outlets were to get hacked, there’s a good chance that you’ll be subject to the old “one to rule them all” method – and all of a sudden, your company’s corporate data is at risk. It’s pretty simple really.
The simplicity of this kind of breach makes MFA – which verifies your digital identity by creating a unique profile by combining your personal biometric data with the device you’re using – is so crucial.
Implementing Last Mile Security
Disclaimer: This is the part of the piece where we throw neutrality to the side. If you’re not ready for a gentle sales pitch, head to the next blog post.
Not all organizations are created equal. In an effort to overcome these remote access threats, some companies arm their remote employees with a full remote suite, complete with a remote gateway, a workstation, and a VoIP phone. Not every business has the resources to make this happen obviously. Those that do often leverage the Meraki Z3 teleworker device, which is effectively a router that employees can bring home, giving them firewall protection and corporate network access via a VPN tunnel.
Now, on top of that, you can choose to deploy a variety of products to help secure the last mile – one for MFA, another for posture assessment for specific cloud applications, and yet another for posture assessment for the cloud.
But why onboard all of that functionality in disparate systems?
Ok, well here’s where the sales pitch happens…in this instance, we recommend Portnox CLEAR because it unites MFA for the remote access, continuous posture assessment and active prevention of security risks – all under one roof. Oh, and did we mention that CLEAR can also work with either/ both managed corporate devices and BYOD?
Try Portnox Cloud for Free Today
Gain access to all of Portnox's powerful zero trust access control free capabilities for 30 days!