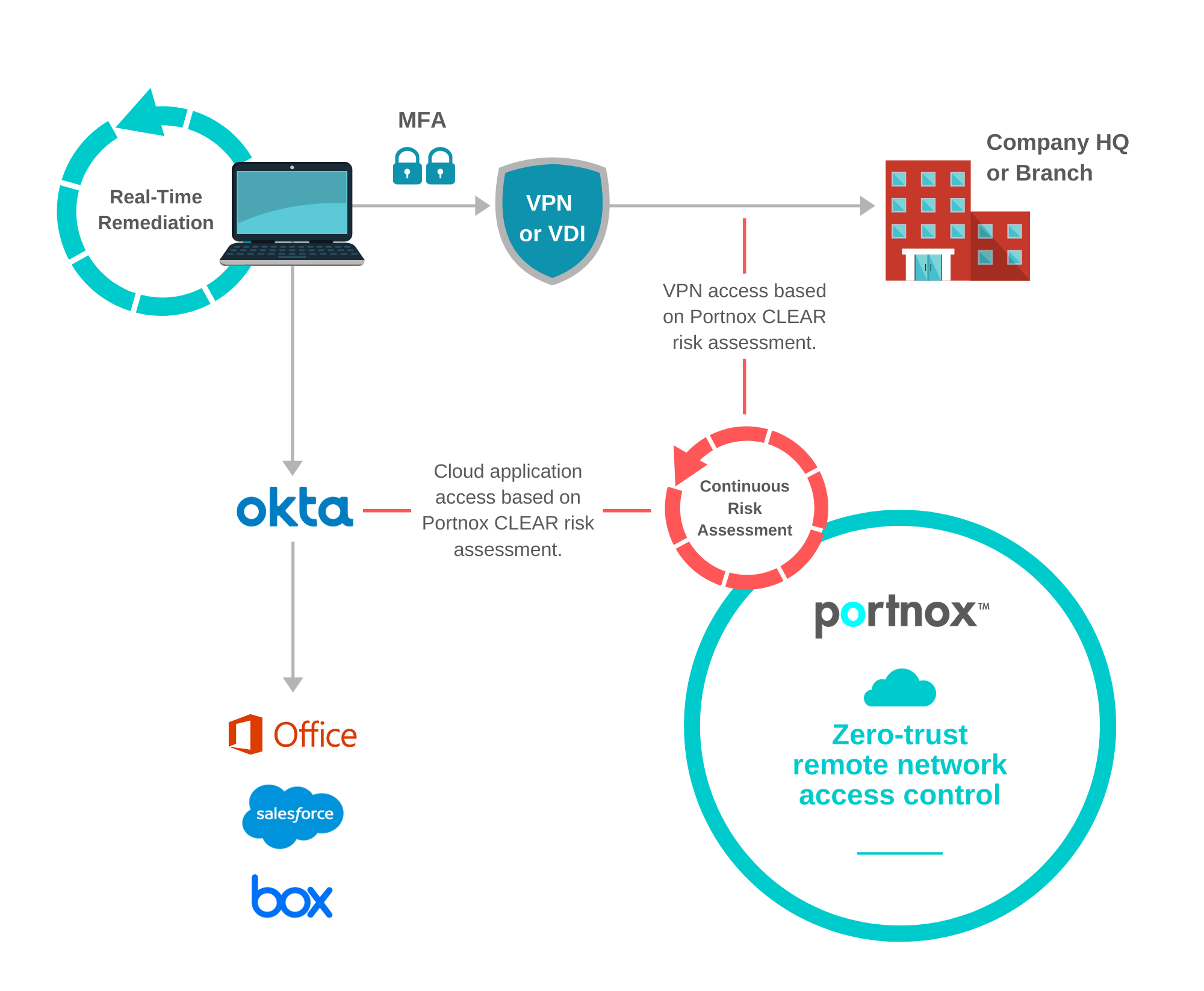
Setting up Secure Remote NAC through VPN & VDI

Any IT team can set-up remote network access with minimal guidance. Without the proper parameters, however, this remote access has the potential to be open to everyone – not just for those it was designed to serve. When setting up secure remote network access control, there are three components to consider: 1) application access, 2) user authentication and 3) the endpoint. Each component has its own unique security considerations to keep in mind.
These considerations include:
- Application Access
- Facilitating access via VPN or VDI
- Defining the authorization policy (e.g. application access for all or by role?)
- Authentication
- Imposing multi-factor authentication (MFA) to defend against stolen credentials
- Endpoint
- Verifying security posture of the endpoint
- Preventing security violations
- Remediating security violations in real-time, automatically
1. Application Access
Generally speaking, there are two kinds of applications employees will need access to. These include “internal” applications and cloud applications. As a means of safeguarding sensitive or proprietary data stored across their various cloud applications, many organizations will institute application access policies that prevent users from directly accessing cloud platforms unless a “tunnel” to the organization is established.
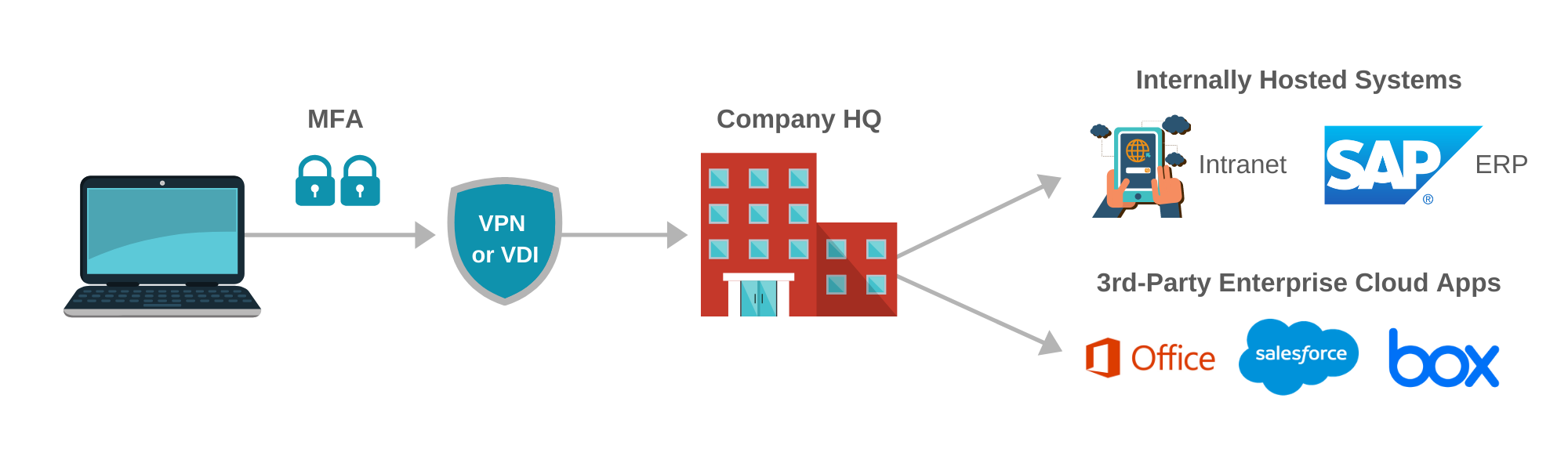
2. Authentication
At the end of the day, your VPN is only as secure as the authentication to it. MFA is mandatory when initiating remote access. Without it, the entire organization, its applications, and data are exposed to theft and possible destruction. MFA can be operationalized in many forms – SMS, tokens or push notifications. Ultimately, it serves as means of authenticating a user beyond that user’s password. Thus, if a user’s password is compromised, no harm can be done. Lastly, in order to access the organization’s network, you need an endpoint. A computer – running Windows, MAC OS, etc. – or even a tablet or smartphone.
3. Endpoint
The endpoint can be an organizational device such as a company-owned laptop or a personal device. Especially in times of crisis, like during the current Covid-19 outbreak, more and more employers are shifting to bring-your-own-device (BYOD) or personal equipment policies, where employees can now use their own devices to access corporate resources.
If these endpoints are compromised, however, all of the above mechanisms are effectively useless. Malware can spread through the VPN, data can be stolen and harm can be done. This means that ensuring endpoints are in good standing is vital to the health of the organization. It’s like making sure to wash your hands – the best method to avoid viruses (for lack of a better analogy).
Furthermore, the prevention of risky behavior – like inserting a USB disk into your laptop – is important. This also goes for making sure your endpoint detection and response (EDR) and antivirus is always running and up-to-date. It may seem like common sense, but maintaining this baseline discipline will help to minimize or eliminate external threats.
Remote Network Access Control in Action
Portnox CLEAR, our cloud-delivered remote network access control solution, provides that commonly missing security layer over your VPN or VDI. Delivering continuous risk monitoring for your endpoints, whether company-owned or personal, CLEAR can easily transform non-secure endpoints to trusted devices. Through corrective and preventive action capabilities (CAPA), CLEAR prevents a host of distinctive remote access threats and provides unique multi-factor authentication as an added layer of user endpoint security.
Related Reading
Try Portnox Cloud for Free Today
Gain access to all of Portnox's powerful zero trust access control free capabilities for 30 days!