Before you read this blog post, be sure to check out the first part of this series: “Network Access Control – A Bird’s Eye View”” for an introductory read on the vast and wide-ranging topic surrounding Network Access Control (NAC). Originally, NAC was about blocking devices and restricting access, and in many ways, this still rings true.
Internet security specialist, Bruce Shneier blogged about an interesting case that occurred in Israel a few years ago: Thieves had broken into a small bank, but surprisingly, nothing was taken. Investigators assumed that the perpetrators had run away when the alarm was set off, but what they didn’t know, was that the criminals never intended to steal any money – at least not at the time. What they had done, in fact, was connect a rogue access point to the bank’s network, rented an office nearby and deployed the kill chain intrusion methodology with the aim to syphon money from the financial institute.
Avoid the 5 Pitfalls of NAC – Get our Free Whitepaper Today!
Unbeknownst to the intruders, their repeated withdrawal of NIS. 49,999 over a period of time, flagged as an irregular occurrence on the bank’s system. One of the suspects went to the branch to withdraw the money, and that’s when police swooped in. This demonstrates how one single rogue access point can exploit company information assets and place them in very precarious positions.
Classic NAC is about blocking, disconnecting ports and identifying rogue devices on the network. The next evolutionary level of NAC, however, is to quarantine – either by VLAN assignment to a containment VLAN, or by setting an access list (ACL). In rare cases ARP poison (arp spoofing) is used. Each one of these policies has advantages and drawbacks to consider when deploying :
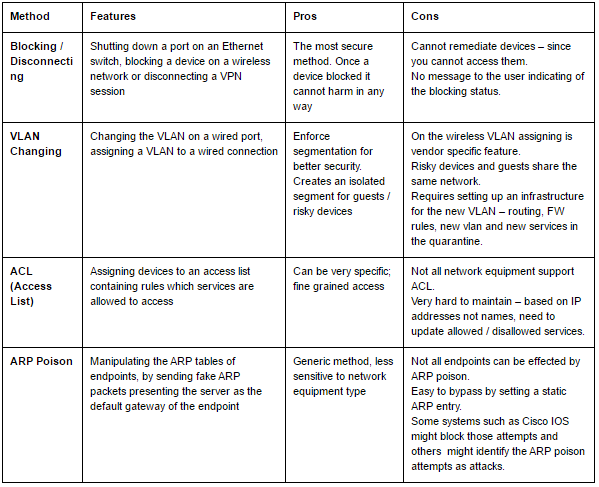
Lastly, the importance of blocking a device, AKA keeping the bad guys out of your network, is entrenched as common practice for all organization. PCI and other standards are quite common for auditors to check.
Try Portnox Cloud for Free Today
Gain access to all of Portnox's powerful zero trust access control free capabilities for 30 days!







