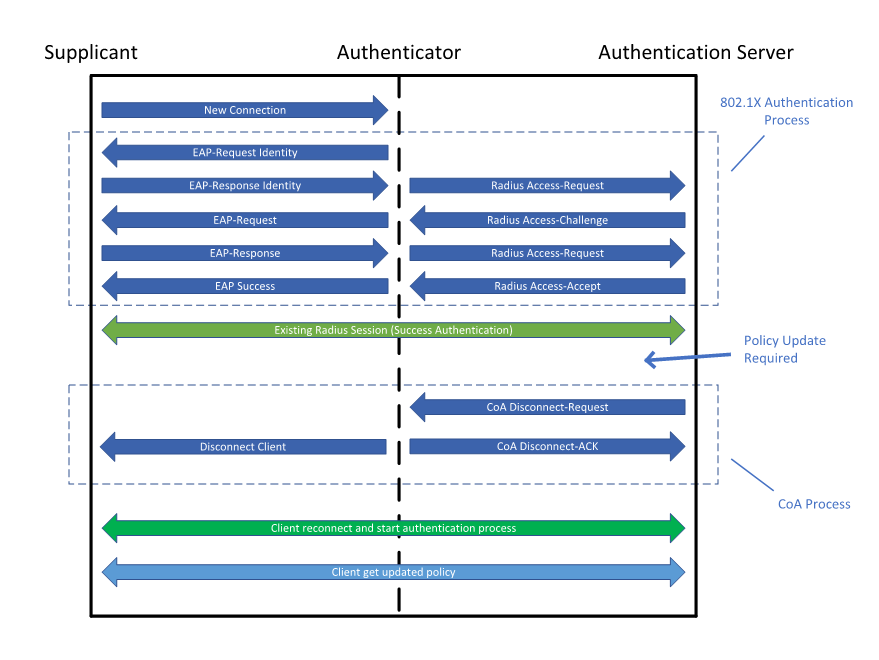
The RADIUS change of authorization (as defined in RFC 5176) provides a mechanism to change authorization dynamically after the device/user is authenticated. Once there is a policy change for a user, you can send RADIUS CoA packets from the authorization server to reinitiate authentication and apply the new policy.
The RADIUS CoA process allows you to change the user access immediately when needed, without the need to wait for the wired switch or access point to initiate a re-authentication process, or for the device to disconnect and re-connect again.
CoA use cases (for connected authenticated devices) include:
- Access control policy update, such as VLAN assignment for a group of devices/users
- Risk/posture assessment policy was updated for a group of devices/users
- Administrator blocked a device/user
- Device risk score/compliance changes: Device is out of compliance (such as AntiVirus or firewall was turned off), thus needs to be set to quarantine VLAN or have access completely blocked; Or device is back in compliance, thus needs to be set to the production VLAN.
The CoA process functions as follow:
- A device is connected to a wired ethernet switch or WiFi SSID after a successful authentication
- There was a policy update or a change on the endpoint which requires that the device completely disconnect from the network or reconnect with different access than the current one (i.e. different VLAN, apply ACL)
- The RADIUS server sends the CoA packet to disconnect the device which leads to re-authentication and applies the new access policy
CoA Packets
The RADIUS CoA packet is sent on port UDP 3799 or UDP 1700 – as used by some network vendors.
Disconnect-Request (PoD – Packet of Disconnect) is a request being sent to the NAS – Network Access Server (i.e. switch/access point), in order to terminate the user session/s. As a reply, two packets can be sent from the NAS:
- Disconnect-ACK – acknowledgment, successful disconnect
- Disconnect-NAK – negative acknowledgment, disconnect session failed
A CoA-Request packet can also be sent to initiate changes on the device or port such as re-authentication and bounce port. As a reply, two packets can be sent from the NAS: CoA-ACK (successful CoA action acknowledgment) and CoA-NAK (CoA failed action). When there’s a need for a VLAN change, using CoA-Request, might not force the endpoint IP address to be released and renew. Instead, it may only change the VLAN. Thus, for implementations that require VLAN change, it’s recommended to use the Disconnect-Request CoA packet which will lead to re-authentication, and for the device to get a new IP address on the updated VLAN.
CoA Disconnect-Request with 802.1X RADIUS Authentication Flow
 RADIUS Change of Authorization Packet Capture
RADIUS Change of Authorization Packet Capture
CoA RADIUS codes
| CoA Packet | Radius Code |
| Disconnect-Request | 40 |
| Disconnect-ACK | 41 |
| Disconnect-NAK | 42 |
| CoA-Request | 43 |
| CoA-ACK | 44 |
| CoA-NAK | 45 |
Packets Capture Examples using Wireshark
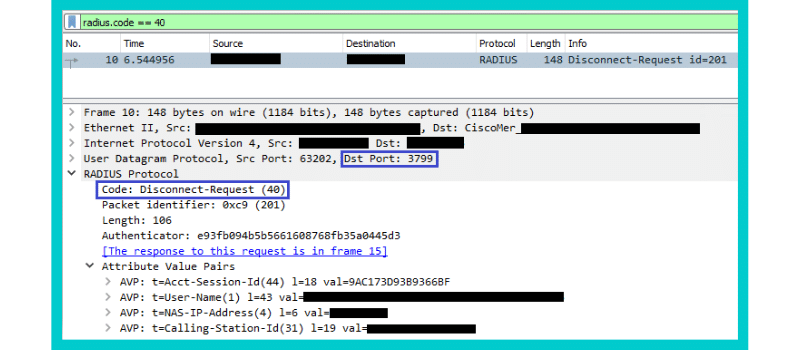
Disconnect-Request:
Disconnect-ACK:
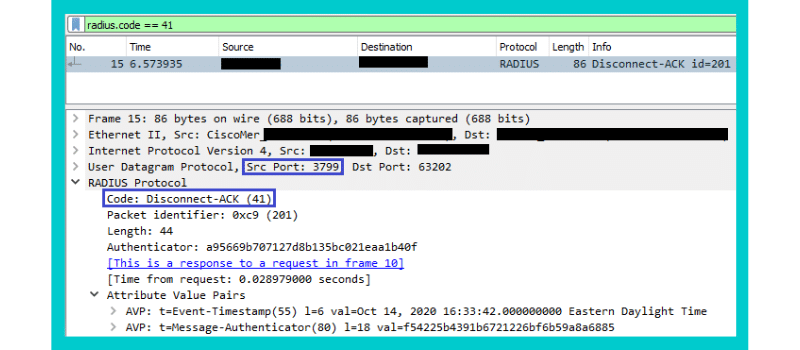
These packets contain attributes with information on the NAS (wired switch/access point), endpoint involved, timestamp, and a link to the frame of the RADIUS server requests / NAS responses.
RADIUS Change of Authorization with Portnox CLEAR
Using Portnox CLEAR for CoA with dynamic VLAN assignment (previously discussed in Dynamic VLAN Assignment) implementation, allows the administrator to achieve a secure and segmented network for dynamic changes in the environment. Whether it’s an access policy change for a group of users/devices or a compliance change on a specific endpoint, the device(s) will be immediately placed on the relevant network, or blocked according to the policy.
Try Portnox Cloud for Free Today
Gain access to all of Portnox's powerful zero trust access control free capabilities for 30 days!







