Portnox Cloud
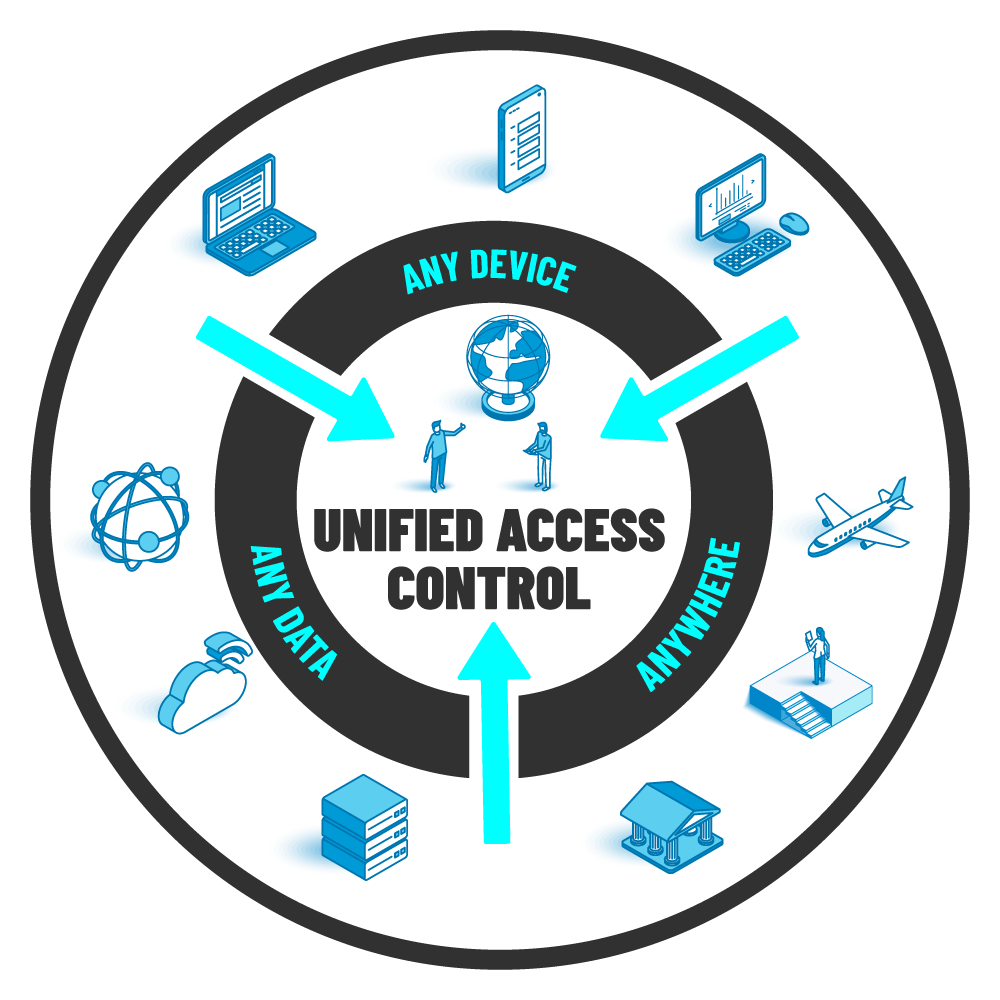
THE ONLY CLOUD-NATIVE PLATFORM FOR UNIFIED ACCESS CONTROL COVERING ANY DEVICE, ANY DATA, ANYWHERE.
This is the Portnox Cloud - the first cloud-native platform that unifies passwordless authentication, zero trust access control, risk mitigation, and compliance enforcement for networks, applications, and infrastructures.
Cloud-native zero trust access control essentials.
The Portnox Cloud delivers the best value in cyber security today, enabling companies to implement zero-trust across several areas of their security stack simultaneously. But that’s not all – easy deployment and scalability paired with no maintenance make Portnox headache-free, freeing up your IT security team to tackle other priorities.
Unified
Control access to your network, applications, and infrastructure - all under one roof.Cloud-Native
The Portnox Cloud is fully cloud-native, making it easy to scale and manage.Vendor Agnostic
Apply access controls to any networking hardware or applications in use.Maintenance-Free
Never lose sleep over upgrades, patches, or costly maintenance ever again.The fastest, most effective way to achieve zero trust across the organization.
Let’s be honest – zero trust is an over-marketed buzzword with seemingly little tangible applicability. That ends today. The Portnox Cloud supports several key tenants of zero trust and applies to an array of real-world use cases.
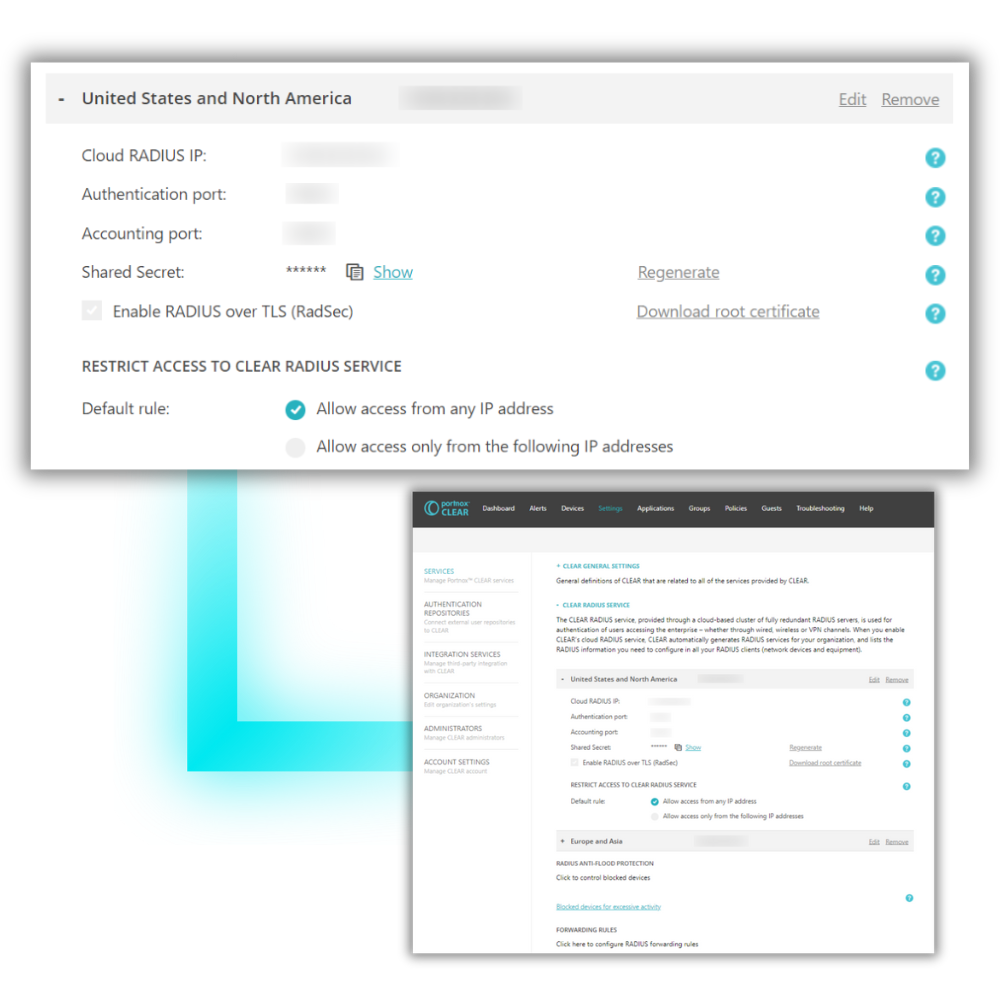
RADIUS authentication has never been so seamless or easy to deploy.
After standing up our cloud RADIUS server in 30 minutes or less, you’ll wonder why you ever messed with that on-prem stuff to begin with. Simple, secure network authentication for all access layers is just a click away.
Scalable zero trust network access control you can bet the farm on.
Spending any amount of time configuring, installing, or patching an on-prem solution like Cisco Identity Services Engine (ISE) or Aruba ClearPass will quickly open your eyes to why cloud-native network access control (NAC) is the future. Get the network authentication, access control, risk mitigation, and compliance enforcement capabilities you need without the hassle or cost of legacy vendors.
Passwordless conditional access for applications.
Sure, your networks are important, but your SaaS applications are in use everywhere, all the time, by employees, guests and contractors. They deserve some love, too. Explore the new and exciting world of zero trust conditional access for applications. You’ll end up asking yourself: why didn’t I consider this earlier?
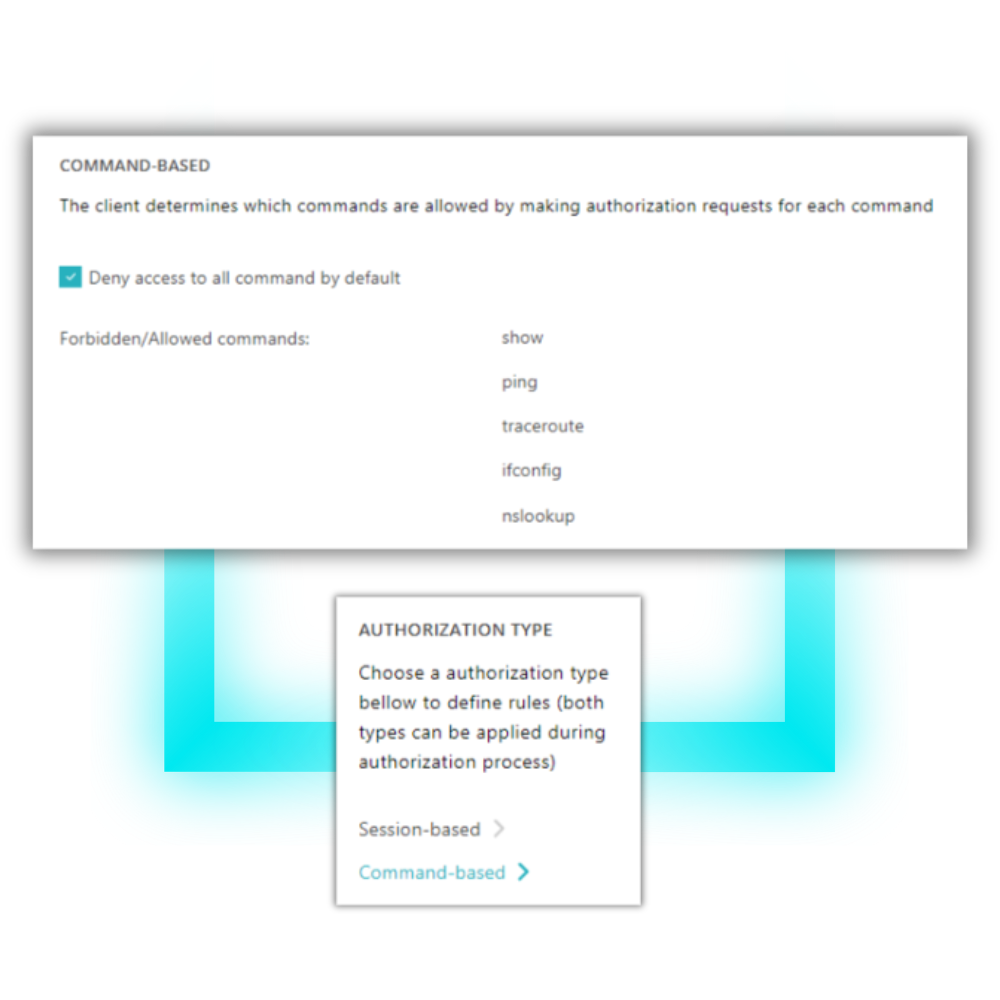
Keep auditors happy & cover your AAA with cloud-native TACACS+.
Discover the power of Portnox's TACACS+ and elevate your infrastructure management, no matter the scale — from a cozy 10 devices to a towering 10,000. Embrace the full suite of advantages with our cloud-native platform, where implementing least-privileged access becomes as detailed as controlling individual commands. Enjoy effortless harmony with your existing security tools and identity providers for a seamlessly integrated experience. And say goodbye to those disruptive late-night upgrades or patches. With Portnox, you're not just managing your network; you're mastering it with ease and efficiency.