Portnox White Paper
Securing Network Access in an SD-WAN World

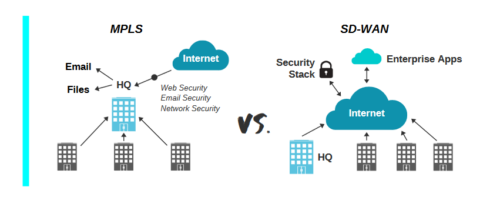
Why SD-WAN, Why Now?
The rise of Software-as-a-Service (SaaS) and cloud services is resulting in decentralized data traffic flows, in turn rendering the traditionally expensive Mutliprotocol Label Switching (MPLS) inefficient for wide area network (WAN) transport.
The emergence of software-defined WAN (SD-WAN) in response to rising cloud adoption is significant because it promises to deliver reduced cost and enhanced performance and availability. This is a trend that is unlikely to go away. In fact, it’s set to intensify. According to Gartner. SaaS and Infrastructure-as-a-Service (IaaS) will grow at 17% and 27%, respectively, through 2022. Both are key drivers of SD-WAN adoption in that time.
The Impact of SD-WAN on Network Security
Today, organizations can leverage SD-WAN technology to implement software-defined branch (SD-branch) as a way of extending IT environments to any of its branches outside of its headquarters that require high-quality network connectivity.
For retailers, hospitality groups (hotels, restaurants, etc.), commercial banks and other large distributed organizations, SD-branch is particularly useful as it utilizes SD-WAN technology to simplify a branch’s IT architecture – reducing the resources and budget needed to maintain operations.
Branches are typically more at risk of network threats than organizational headquarters due to the fact that they’re inherently understaffed or underserved from an IT standpoint.
Network Access in an SD-WAN World
The rise of BYOD, mobile workforces and IoT has driven an exponential increase in the number and types of devices that can connect to today's corporate networks. Securing and protecting these devices - particularly agentless IoT devices - is a core principal and best practice in cyber security.
Today, device segmentation (especially for IoT) has evolved to become the only effective option for network defense, as it enable organizations to protect themselves against lateral movements and to detect network breaches faster.