Common Endpoint Vulnerabilities that Create Risk for Corporate Networks

Attack methods that exploit endpoint vulnerabilities are evolving, and network security teams are scrambling to keep pace. These endpoints, which include devices like laptops, smartphones, and IoT devices, can often serve as entry points for cybercriminals. Today, we explore common endpoint vulnerabilities that pose risks to corporate networks and how Network Access Control (NAC) can help mitigate these vulnerabilities to enhance overall security.
Understanding Endpoint Vulnerabilities
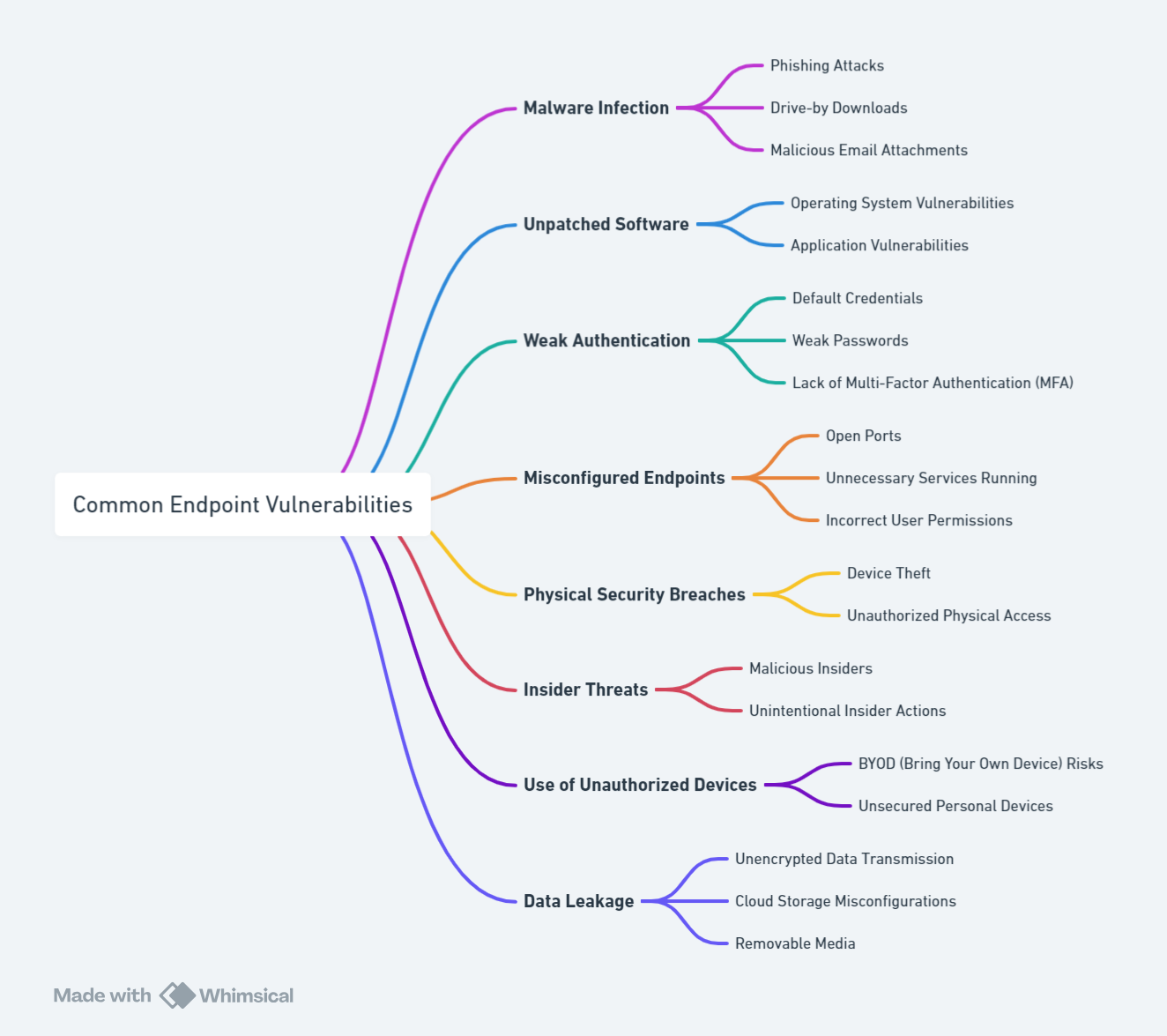
Endpoints refer to devices that connect to the corporate network, including laptops, smartphones, tablets, and other IoT devices. These endpoints can become the weakest link in network security, offering cybercriminals a gateway to infiltrate corporate systems. Some of the most common endpoint vulnerabilities include:
- Malware Infection: Endpoints can be compromised through phishing attacks, drive-by downloads, and malicious email attachments, leading to malware infections that can spread across the network.
- Unpatched Software: Vulnerabilities in unpatched operating systems and applications can serve as entry points for attackers.
- Weak Authentication: The use of default credentials, weak passwords, and the absence of Multi-Factor Authentication (MFA) can make endpoints easy targets.
- Misconfigured Endpoints: Open ports, unnecessary services, and incorrect user permissions can expose networks to unauthorized access.
- Physical Security Breaches: The theft of devices or unauthorized physical access can lead to direct network infiltration.
- Insider Threats: Actions by malicious insiders or unintentional mistakes by employees can compromise network integrity.
- Use of Unauthorized Devices: BYOD (Bring Your Own Device) policies and unsecured personal devices can introduce vulnerabilities.
- Data Leakage: Unencrypted data transmission, cloud storage misconfigurations, and the use of removable media can lead to data exposure.
These vulnerabilities highlight the need for robust security measures that can protect endpoints and, by extension, the entire corporate network.
The Role of Network Access Control (NAC) in Mitigating Risks
Network Access Control (NAC) is a security solution that enforces policy-based access control for devices attempting to connect to the network. NAC can identify, evaluate, and remediate endpoint vulnerabilities in real-time, thereby enhancing network security. Here’s how NAC can help mitigate the risks associated with common endpoint vulnerabilities:
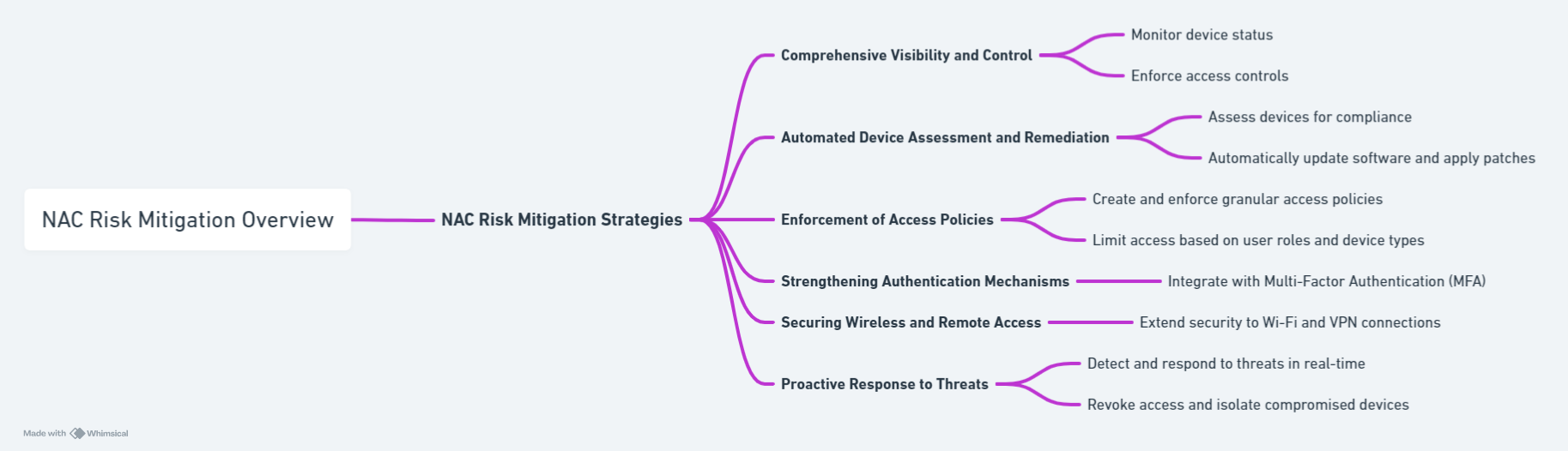
1. Comprehensive Visibility and Control
NAC solutions provide complete visibility into all devices connected to the network, including BYOD and IoT devices. This visibility allows IT administrators to monitor device status, ensure compliance with security policies, and enforce access controls based on device posture and user credentials.
2. Automated Device Assessment and Remediation
Upon attempting network access, devices are assessed for compliance with the organization’s security policies. NAC can automatically remediate non-compliant devices by updating software, applying patches, or directing them to a quarantine network until they meet the necessary security standards.
3. Enforcement of Access Policies
NAC enables the creation and enforcement of granular access policies based on user roles, device types, and other criteria. This ensures that devices and users only have access to network resources essential to their roles, minimizing the risk of insider threats and data leakage.
4. Strengthening Authentication Mechanisms
By integrating with Multi-Factor Authentication (MFA) systems or by leveraging digital certificates, NAC adds an additional layer of security for device and user authentication. This significantly reduces the risks associated with weak authentication practices.
5. Securing Wireless and Remote Access
NAC solutions extend their security capabilities to wireless networks and remote access scenarios, ensuring that devices connecting via Wi-Fi or VPN are subject to the same stringent security checks as wired connections.
6. Proactive Response to Threats
Advanced NAC systems can detect and respond to threats in real-time. If a device is found to be compromised or acting maliciously, NAC can immediately revoke network access, isolate the device, and alert administrators, thereby preventing the spread of malware or the escalation of an attack.
Implementing NAC: Best Practices
To maximize the effectiveness of NAC in mitigating endpoint vulnerabilities, organizations should consider the following best practices:
- Comprehensive Policy Development: Develop clear, comprehensive policies that define acceptable use and security requirements for all types of devices and users.
- Regular Audits and Compliance Checks: Conduct regular audits of device compliance and security posture to ensure ongoing adherence to security policies.
- Integration with Other Security Solutions: Integrate NAC with existing security solutions, such as firewalls, intrusion detection systems (IDS), and security information and event management (SIEM) systems, for a layered defense strategy.
- User Education and Awareness: Educate users about security policies, the importance of compliance, and the role they play in maintaining network security.
As the threat landscape evolves, so too must the strategies to combat these threats. Endpoint vulnerabilities represent a significant risk to corporate networks, but with the implementation of Network Access Control (NAC), organizations can significantly enhance their network security posture. By providing comprehensive visibility, enforcing strict access controls, and automating the remediation of non-compliant devices, NAC serves as a critical component in the defense against cyber threats. Through diligent implementation and adherence to best practices, organizations can leverage NAC to protect their networks and ensure the integrity of their digital assets.
Try Portnox Cloud for Free Today
Gain access to all of Portnox's powerful zero trust access control free capabilities for 30 days!






