Tackling Device Access with Custom TACACS+
A Short History of Everything TACACS+
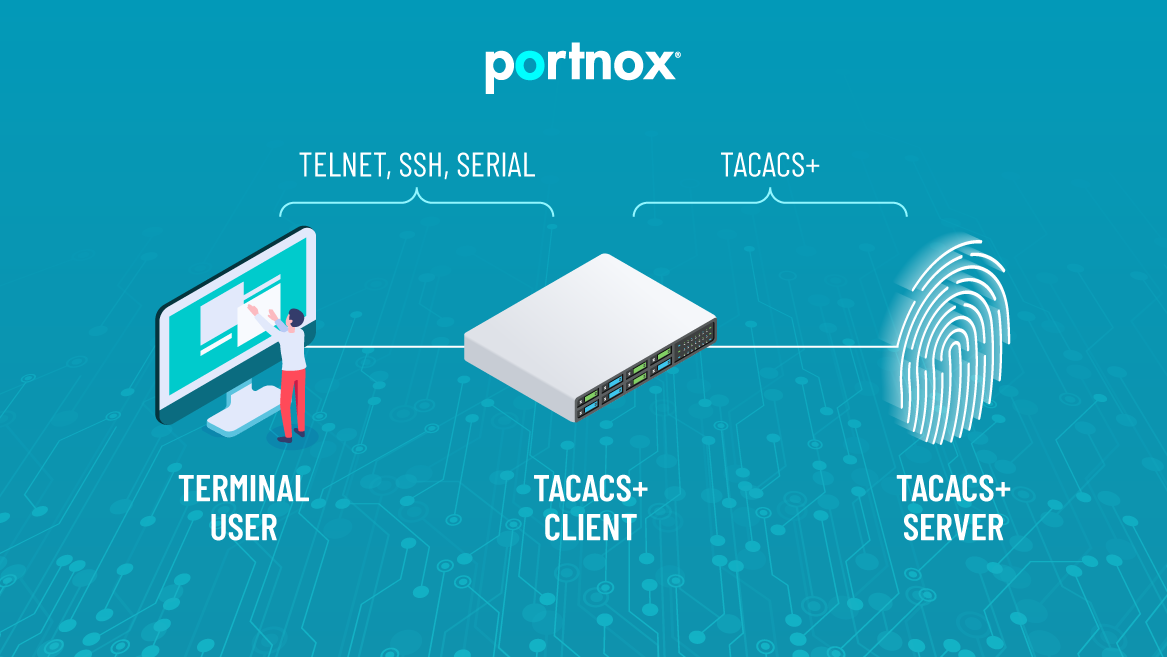
Before we talk about how custom TACACS+ login integration works, we should delve into a little history. Terminal Access Controller Access-Control System (known as TACACS to its friends) was developed in 1984 by a group of people who realized long before the internet was a thing that having to manage multiple devices is a huge pain. It was replaced (or rather, extended) by TACACS+ in 1993, which means TACACS has been making life easier for IT Admins for almost 40 years! When you have multiple devices to manage, tracking separate logins for each one is exhausting. People tend to sacrifice security for the sake of simplicity – using a shared set of credentials for all network devices, for example, or just giving everyone blanket admin permissions rather than tailoring access to meet the needs of what each person needs to do. The need for a simplified protocol to handle all of this was readily apparent, and the idea for centralized authentication was born – what if there could be a centralized server that would handle authentication, and rather than creating a bunch of individual accounts on each network device, the devices could just check in with that server and see if the account was valid?
Adding A’s to Authorization
Once the problem of logging in was solved, ideas for other things TACACS could do were generated. Beyond just simple Authentication (Are you allowed in – y/n?) the idea for TACACS integration with Authorization (what are you allowed to do now that you are here?) was a natural extension. As an example, Cisco devices have 16 levels of privilege, ranging from level 0 (limited to a very few basic show commands) to level 16 (I am the alpha and omega of this device.) With TACACS, rather than just assigning a user a blanket enable level and hoping that covers them while also hoping you didn’t just give them the ability to destroy your entire network, you can assign individual commands to users. This is huge, as it allows you to keep your security posture strong by not giving away more rights than necessary while also letting people do their jobs. After that, the final piece of the puzzle was Accounting – what did you do while you were here? We like to think that was invented by a network admin who got really tired of blank stares when he asked “Ok, who changed the startup config?!” after a network outage.
Custom TACACS+ Login Integration
As awesome as TACACS+ is, IT Administration does not happen in a vacuum. Having a separate set of credentials for a TACACS environment is certainly easier than having logins for every device, but it’s still one more password you have to deal with remembering, forgetting, and resetting. With the average person having over 100 passwords to worry about, it’s fair to say the number of passwords is getting out of hand. Portnox wants to make your IT life easier, and that’s why our cloud-native TACACS+ offers custom tacacs+ login integration with your existing identity providers. All the work you’ve put into your Google Workspace, Okta, or Azure AD directory structure will carry over seamlessly into your TACACS environment, so you don’t have to spend time setting up something new and adding just one more account to manage. Contact us for a demo today and see how Portnox can make your IT life easier!
Try Portnox Cloud for Free Today
Gain access to all of Portnox's powerful zero trust access control free capabilities for 30 days!