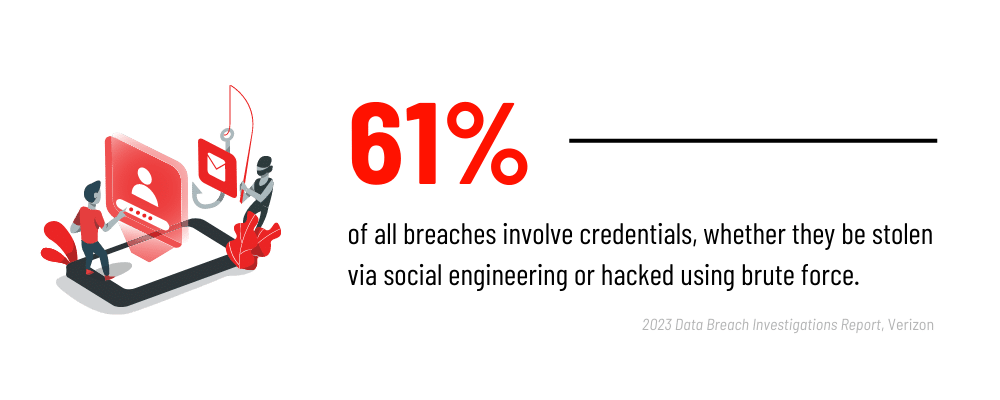
Passwords have long been a weak link in the security chain. They can be easily guessed, stolen, or cracked through various malicious techniques. Passwordless login methods eliminate the reliance on passwords altogether, significantly enhancing security. By employing advanced technologies such as public-key cryptography, companies can implement strong authentication protocols that are resistant to brute-force attacks, phishing attempts, and credential stuffing.
Considering Passwordless Login? Here’s What You Need to Know…
When implementing passwordless login methods for network authentication, cybersecurity professionals should consider the following key factors:
I. Strong Authentication Protocols
Passwordless authentication should employ strong authentication protocols, such as public key cryptography. These protocols add an extra layer of security beyond just passwords and provide more robust protection against unauthorized access.
II. Secure Credential Storage
With passwordless login, sensitive credentials like private keys can be used. It is crucial to ensure secure storage of these credentials, either through encrypted cloud-based storage solutions or hardware-based security modules if necessary. Unauthorized access to these credentials could lead to serious security breaches.
III. User Experience and Adoption
Passwordless methods should be designed with a focus on user experience to encourage adoption. Complex or cumbersome authentication processes can result in user resistance or workarounds that compromise security. Balancing security and usability is crucial for successful implementation.
IV. Robust Identity Verification
Passwordless login should include robust identity verification mechanisms to ensure that the person requesting access is indeed the legitimate user. This can involve factors such as device attestation or contextual information like location or network patterns to establish trust.
V. Monitoring and Logging
It is essential to implement monitoring and logging mechanisms to track authentication events and detect any suspicious or malicious activities. Security professionals should have visibility into the authentication process to identify potential threats and respond promptly to security incidents.
VI. Continual Security Updates and Patches
Passwordless methods, like any other security solution, may have vulnerabilities that could be exploited by attackers. Vulnerability assessments should be conducted to ensure that the authentication system remains resilient against emerging threats. Cloud-native solutions can help eliminate the need for continuous patching, updating and general system maintenance.
VII. Backup and Recovery Mechanisms
Implementing passwordless login should also include considerations for backup and recovery mechanisms. In the event of system failures or credential loss, there should be processes in place to restore access securely and without compromising security.
VIII. User Education and Awareness
Introducing passwordless methods requires educating users about the new authentication methods, their benefits, and best practices. Users should understand the security implications, potential risks, and how to properly use and protect their credentials to maintain a strong security posture.
IX. Threat Modeling and Risk Assessment
Before implementing passwordless authentication, conducting a comprehensive threat modeling and risk assessment is critical. This helps identify potential threats, vulnerabilities, and risks associated with the chosen authentication methods and allows for the implementation of appropriate security controls.
The Future of the Passwordless Login Trend
As the workforce adopts new habits and technologies and cyber threats evolve in parallel, the adoption of passwordless login methods for security authentication is gaining momentum. By eliminating the weaknesses of traditional passwords, companies can enhance security, streamline user experience, and meet compliance requirements. Passwordless authentication provides a robust and convenient solution for organizations seeking to protect sensitive data, accommodate mobile workforces, and reduce the costs associated with password management.
Embracing this innovative approach empowers companies to strengthen their security defenses, adapt to the changing work environment, and stay resilient in the face of evolving cyber threats.
Try Portnox Cloud for Free Today
Gain access to all of Portnox's powerful zero trust access control free capabilities for 30 days!