Understanding the Current SASE Framework & Where Cloud-Native NAC Fits In
For years, enterprises have been in a tug-of-war between security and usability. The cloud made IT environments more flexible, but it also introduced new attack surfaces. Remote work and hybrid offices made perimeter-based security nearly obsolete. Enter Secure Access Service Edge (SASE)—a concept introduced by Gartner in 2019—designed to merge security and networking into a unified, cloud-delivered model.
But where does Network Access Control (NAC) fit into this evolving paradigm? Traditional NAC solutions were designed for on-prem environments, but with SASE pushing enterprises toward cloud-first, borderless security, NAC has also undergone a transformation. Cloud-native NAC now plays a crucial role in securing device and user access as part of a SASE framework.
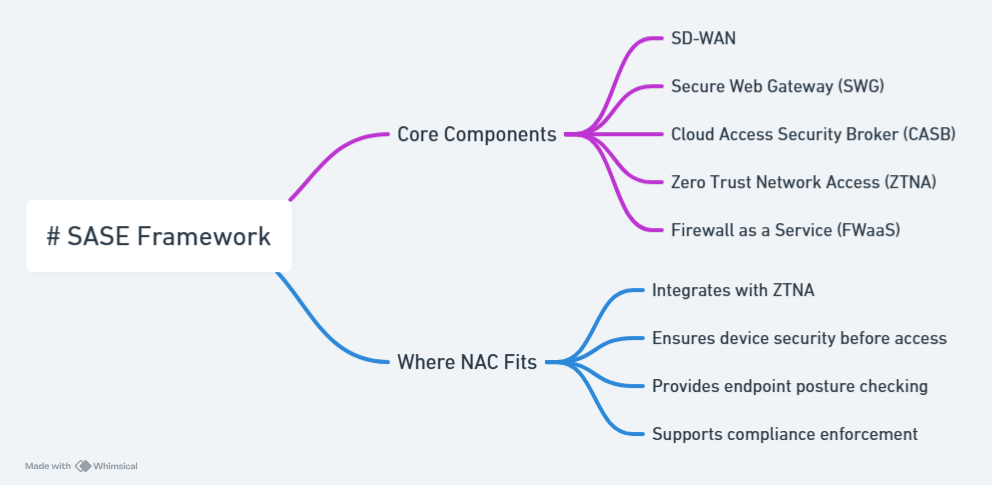
What Does the Current SASE Framework Look Like?
At its core, SASE consolidates network security functions and WAN capabilities into a single, cloud-delivered architecture. Organizations no longer have to rely on siloed security tools deployed at different points in their network—SASE integrates these capabilities to deliver seamless, scalable security regardless of user location.
A modern SASE framework typically includes:
1. Secure Web Gateway (SWG)
A cloud-based filtering and security mechanism that protects users from malicious websites, malware, and phishing attempts, even when they’re outside the traditional network perimeter.
2. Cloud Access Security Broker (CASB)
A policy enforcement point that provides visibility and control over data stored in and accessed from SaaS applications.
3. Zero Trust Network Access (ZTNA)
The replacement for traditional VPNs, ensuring that access to applications and services is granted based on identity, device health, and security posture, rather than IP addresses or network locations.
4. Firewall as a Service (FWaaS)
A cloud-delivered firewall that applies enterprise-grade security policies across remote and branch locations.
5. Software-Defined WAN (SD-WAN)
Optimized networking for remote locations, allowing for intelligent traffic routing based on application needs, security, and performance metrics.
All of these components work together to provide secure access no matter where users are connecting from—be it a corporate office, a coffee shop, or their home WiFi. But what’s often overlooked in this framework is how devices actually connect to the network in the first place. This is where modern cloud-native NAC comes in.
How Cloud-Native NAC Fits into SASE
The Challenge of Network Access in a SASE World
The traditional assumption was that if a user passed identity-based authentication (e.g., logging in via Single Sign-On), they were trusted. But SASE demands more than just identity checks—it requires a Zero Trust approach that assesses device security, compliance, and risk posture before granting access.
This is where cloud-native NAC plays a pivotal role in SASE by ensuring that only compliant and authorized devices—corporate and personal—can access network resources, whether in the office or remotely.
Key Contributions of Cloud-Native NAC to SASE
-
Identity & Device Posture Validation
- Traditional NACs relied heavily on on-prem appliances and static policies.
- Cloud-native NAC integrates real-time posture assessments—ensuring devices meet security requirements before connecting to corporate networks or cloud applications.
-
Agentless, Cloud-Delivered Access Control
- Legacy NAC required agents, complex integrations, and high-touch configurations.
- Cloud-native NAC enables agentless enforcement via cloud-based policies, without requiring additional software on endpoints.
-
Seamless Integration with ZTNA & Conditional Access
- ZTNA focuses on user-to-application security, but it lacks visibility into device compliance.
- Cloud-native NAC bridges this gap by enforcing device security before allowing ZTNA connections to occur.
-
Granular & Adaptive Policy Enforcement
- Devices that fail security checks (e.g., unpatched OS, missing EDR) can be quarantined or denied access, even if the user has valid credentials.
- Adaptive policies allow enterprises to fine-tune access based on risk levels and security posture.
-
Eliminating Blind Spots in IoT & BYOD
- Traditional NAC solutions struggled with unmanaged devices like IoT and personal employee laptops.
- Cloud-native NAC solutions provide full visibility into connected devices, enforcing policies even on headless IoT endpoints.
Why Cloud-Native NAC is Essential for the Future of SASE
The reality is that modern enterprises cannot rely solely on ZTNA, CASB, and SWG to ensure secure network access. Organizations need a solution that verifies not just who is connecting, but what device they are using, its security posture, and where it is connecting from—before granting access.
Cloud-native NAC aligns with SASE’s cloud-first, identity-centric approach to security by:
- Providing Zero Trust-aligned access control
- Eliminating legacy on-prem NAC appliances
- Enforcing device security without additional agents
- Reducing attack surfaces created by unmanaged or non-compliant devices
As SASE adoption continues to rise, enterprises that ignore NAC as part of their security strategy will face significant security gaps. NAC is no longer just about wired/wireless network access; it is about delivering comprehensive access security across hybrid, cloud-first environments.
Final Thoughts
The SASE framework has evolved significantly over the last five years, integrating key security and networking capabilities into a scalable, cloud-native model. While many focus on components like ZTNA, CASB, and SD-WAN, cloud-native NAC is the missing link that ensures devices and users are verified, compliant, and secure before gaining access.
As organizations modernize their cybersecurity posture, adopting cloud-native NAC alongside SASE will be crucial to achieving true Zero Trust security. If your enterprise is moving towards SASE, but you haven’t yet considered a cloud-native NAC solution, it might be time to revisit your access control strategy before security blind spots come back to bite you.
Try Portnox Cloud for Free Today
Gain access to all of Portnox's powerful zero trust access control free capabilities for 30 days!