What Kind of WiFi Protected Access Should You Use to Secure Your Enterprise?

When examining WiFi security, the first layer of defense is the method being used to authenticate to the network. The most widely used methods of authentication are Open authentication, WPA2-PSK (Pre-Shared Key) and WPA2-Enterprise (read more about WPA protocols below). Below, we examine these different options for WiFi protected access.
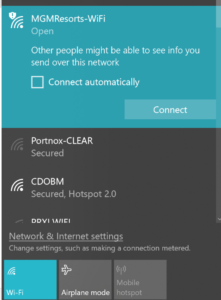
WiFi Protected Access: Open Authentication
As the name implies, an open authentication network allows access to all, and users are not required to authenticate at the association level. It is important to know that open networks are not encrypted, and so everything transmitted can be seen by anyone in its vicinity.
The best security practice is to completely avoid connecting to open networks. If there is an immediate need to connect, it is best not to allow devices to connect automatically but rather to select the network manually in the device settings. Open networks are easily forged, and hacking tools such as Pineapple use the fact that mobile devices are constantly searching to connect automatically to an open network. These tools perform Man-in-the-middle attacks to steal data such as passwords, credit cards, etc.
WiFi Protected Access: WPA / WPA2 / WPA3
WPA stands for WiFi Protected Access. This authentication method uses different encryption algorithms to encrypt the transport. Therefore, this type of network cannot be forged easily, unlike open networks, and users get privacy. Today, WPA2 is probably the most commonly used method to secure WiFi networks.
Sadly, WPA and WPA2 protocols have been hacked and are considered to be less secure. Performing a WPA2 hack requires a lot of time and is somewhat theoretical. Slowly, we are noticing a move to the WPA3 method, but for that to happen, different infrastructure is needed to support that protocol.
WiFi Protected Access: WPA2-PSK
WPA2-PSK (and WPA3-PSK) is WiFi Protected Access (WPA) with a Pre-Shared Key. In simple terms, it is a shared password to access the WiFi network. This method is commonly used for home and small office WiFi networks. Even in a small office setting, using this method is problematic, because each time an employee leaves the company, the password must be replaced; otherwise, the former employee could still connect to the company WiFi.
Furthermore, employees tend to share the password with guests, visitors and contractors in the building, and you shouldn’t have the whole building connecting to the internet at your expense, risking the security of your data and assets in the process.
WiFi Protected Access: WPA2-Enterprise
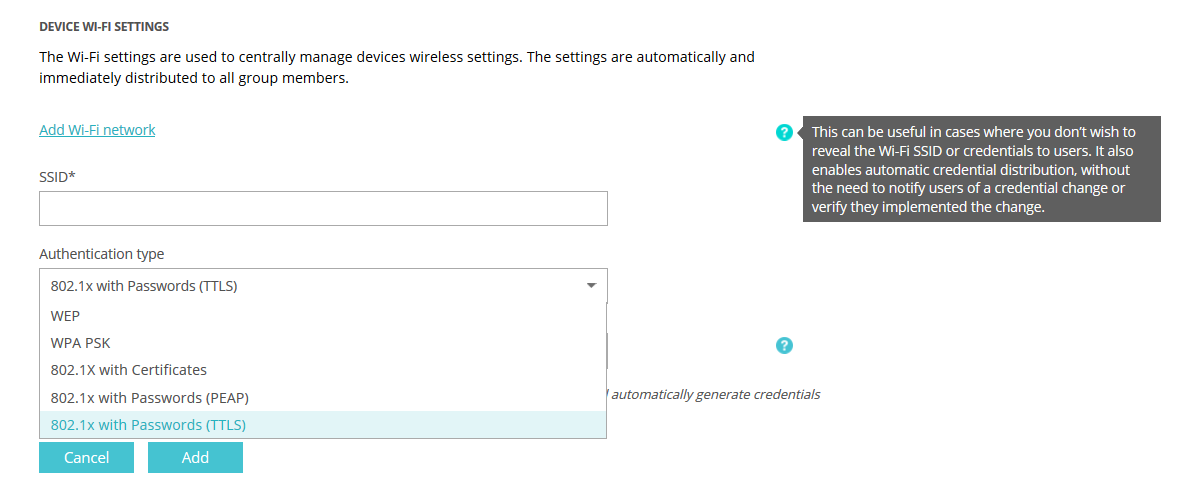
This method, also referred to as WPA-802.1X mode, authenticates to WiFi by using different identities instead of a single password. An identity can be credentials (user + password) or it can be a digital certificate.
This authentication method is better suited for enterprise networks and provides much better security for wireless networks. It typically requires a RADIUS authentication server as well as a configuration process to different repositories, enabling the organization to authenticate different types of endpoints.
The underlying protocols to secure the authentication vary between different Extensible Authentication Protocols such as EAP-TTLS / EAP-TLS, EAP-PEAP, each one representing a different type of authentication method and level of security.
With WPA2-Enterprise one can use advanced features such as assigning each endpoint after authentication to a specific VLAN or assigning ACLs (Access Control Lists) to specific sections. Additionally, enterprises can audit the connection with additional details. These features are important as they allow enterprises to properly secure their wireless networks and to make sure that they are compliant with security best practices.
Try Portnox Cloud for Free Today
Gain access to all of Portnox's powerful zero trust access control free capabilities for 30 days!