Strengthening IoT Security with Cloud-Native DHCP Listening

Enhanced IoT Fingerprinting & Security with Cloud-Native DHCP Listening
More Like the Internet of Everything
With the explosion of new devices connecting to the internet, IoT (or, the Internet of Things) really might as well be called IoE (or, the Internet of Everything.) The use cases for always-connected devices span across industries – from facilities that can now better manage energy usage according to peak customer traffic, and medical devices that can adjust medication levels in seconds, to retail warehouses that can track inventory down to the last widget. It’s undeniable that IoT has been a game-changer.

That’s not to say, however, that IoT does not present some unique challenges – specifically for network security professionals.
Who Are You?
The devices themselves tend to run on extremely lean operating systems, which means they don’t run typical monitoring protocols like SNMP. There’s also no possibility of installing extra software like agents. They’re designed to be easy to set up; just point them at an internet connection, which means any user can add an IoT device.
This creates an especially tough situation for IT administrators. After all, an essential part of zero trust security is knowing what is on your network, which means you need to make sure operating systems and firmware are patched and up-to-date to close the gap on any known vulnerabilities. But how can you know what’s on your network if the devices don’t report back specific identification in any way?
This problem has become so common it has a name – “Shadow IoT” – and it’s so prevalent that 80% of IT leaders found devices on their network they didn’t know about.
IoT Fingerprinting to the Rescue!
To combat this, several companies that make security tools like Network Access Control software have begun offering IoT Fingerprinting. This is a way to gather information about IoT devices like model, OS or Firmware, and manufacturer without requiring the devices to report in. While an absolute game changer for helping secure these devices, it is not without its challenges.
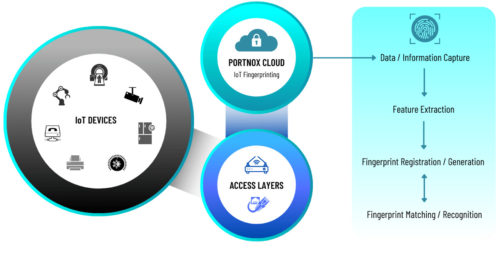
The biggest issue is that there is no real standard across devices – most don’t support Simple Network Management Protocol (SNMP) or Windows Management Instrumentation (WMI). Some devices support Universal Plug & Play (UnPNP) or Bonjour, but typically you only find that on consumer devices like a Roku or an AppleTV. Some Cisco devices support CDP (Cisco Discovery Protocol), but that doesn’t cover other vendors; some may use LLDP instead (Link Layer Discover Protocol) but typically you will find that only on phones, video conferencing equipment, and commercial IP surveillance cameras.
Port scanning via Nmap & TCP have more drawbacks – they scale very poorly. Also, with increased pressure on IoT manufacturers to pay more attention to security, more and more devices are being shipped with all ports turned off. And of course, the most basic firewall will raise alarms when a port scan is detected.
MAC address will get you some information, but they pose some challenges too. The first six hexadecimal digits of a MAC address are called the OUI and they identify the manufacturer. This is useful, but also not super accurate in the sense that if you find an HP device on your network, that does little to tell you what it exactly is. It also does not tell you any information about operating systems or firmware.
DHCP at first seems like a great option – when a device connects to a network, its first step is typically to request an IP from a DHCP server. During the DORA process (Discovery, Offer, Request, Acknowledge) much information is passed back and forth, including information to fingerprint the device. Many enterprise switches support a process called DHCP Gleaning, where the switch listens for DHCP requests Switchport interfaces and is then captured as a device sensor and sent along with RADIUS accounting info.
The problem here is that not all switches support DHCP Gleaning. For the ones that don’t, how do you get the information collected by the DHCP server to your network access control software to do the actual fingerprinting? Some solutions have you install an on-prem DHCP forwarder, which signs your IT team up to deal with deploying and maintaining yet another server, upgrades, patches, etc. Even worse, this separate forwarder creates overhead on your network that may impact your users and sensitive traffic.
So, all hope is lost, and there’s no reliable way to accurately fingerprint all your IoT Devices, but there’s great news coming.
Portnox’s DHCP Listener Heads to the Cloud
Keep all the magic of a cloud-based solution – vendor agnostic, no maintenance, no upgrades, no worries – AND get the most accurate fingerprinting of all your IoT devices as part of your comprehensive zero-trust solution!
You can easily configure your network devices to send the data your DHCP server already gathers throughout the course of handing out IP Addresses to the Portnox SaaS DHCP listener.
All you need to enable is a layer 3 device on the same subnet as the devices you want fingerprinted, that is NOT also acting as a DHCP server. You will need to configure the DHCP helper, which will forward this information to us. Most devices support using a DHCP helper – in fact, most devices support running multiple, so no need to sacrifice anything in your current architecture. The helper will forward DHCP and BOOTP broadcasts on directly connected subnets and relay them to the Portnox DHCP listener on port 67.
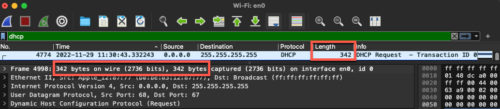
If you have bandwidth considerations, you can lay them to rest – DHCP is a very lightweight protocol, consuming less than 350 bytes per request on average. Since we are not making DHCP offers, the only bandwidth is from the clients DHCP request that is forwarded from the clients.
So let’s say you have 500 clients. A DHCP lease is typically 24 hours, with clients renewing at 12 hours. That means you’d spend 175 kilobytes of total data every 12 hours…even a 28.8 baud modem could handle that request.
We use this formula to calculate bandwidth:
(((TOTAL # OF DHCP CLIENTS X 350BYTES) X2 FOR 24 HOURS) X8 CONVERT TO BITS)/ 86400 SECONDS IN A DAY
IN EXCEL THE EQUIVALENT FORMULA WOULD READ: =(((500 *350)*2)*8)/86400
This first-of-its-kind SaaS DHCP listener is easy to set up, and opens a whole new world of accurate fingerprinting for IoT Devices – click here to get started!
Try Portnox Cloud for Free Today
Gain access to all of Portnox's powerful zero trust access control free capabilities for 30 days!