Easy to Use,
Simple to Manage
Cloud NAC
Network access control, now available as SaaS.
Purpose-built for today's distributed enterprises.
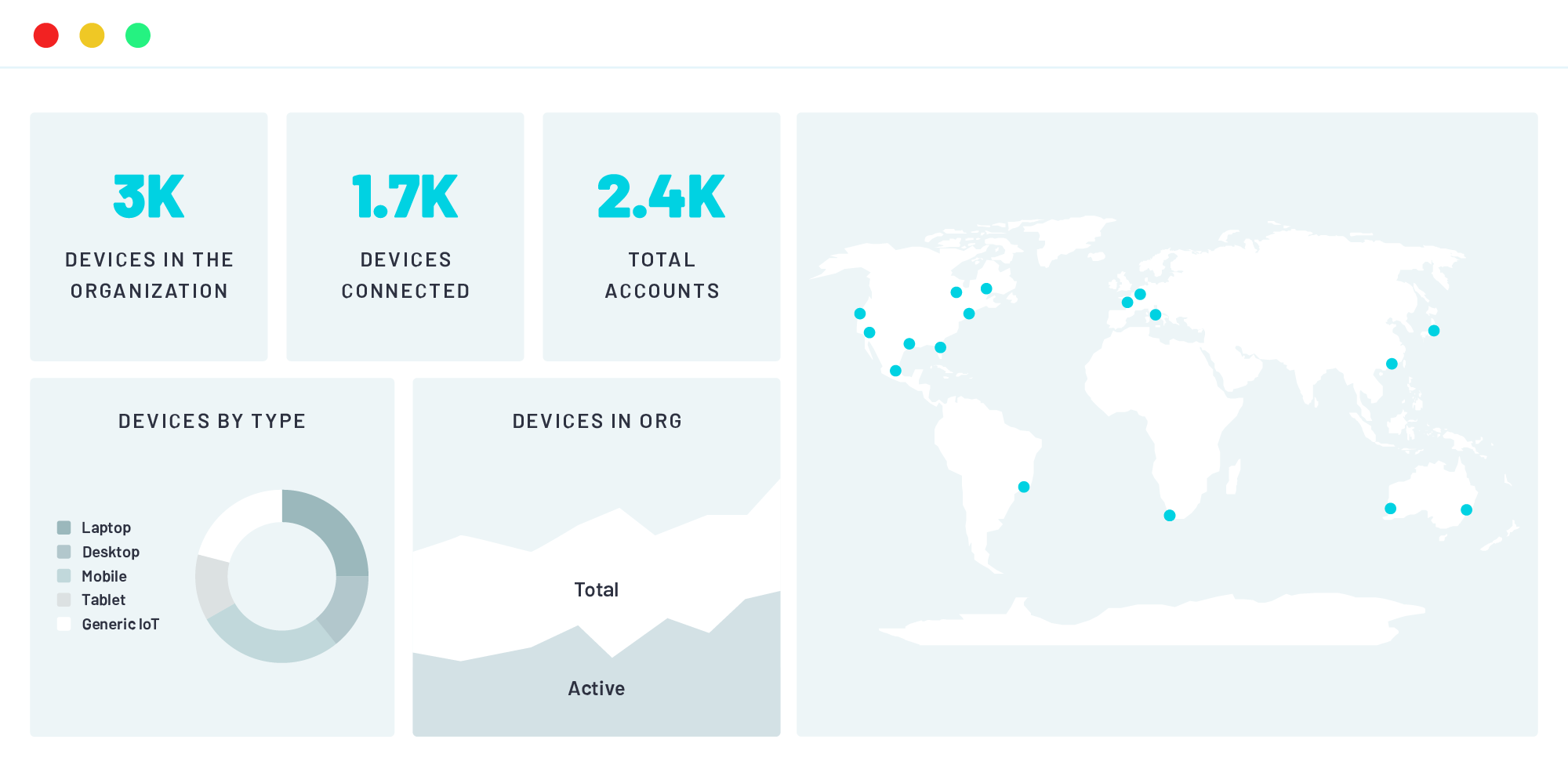
Simplicity, Scalability & Savings. Out of the Box.
Get Out of the Ice Age &
Replace Your Legacy,
On-Prem NAC Today
Save time and lower your total cost of ownership by eliminating on-going maintenance, upgrades, network downtime, end-of-life costs and more typically associated with traditional NAC.
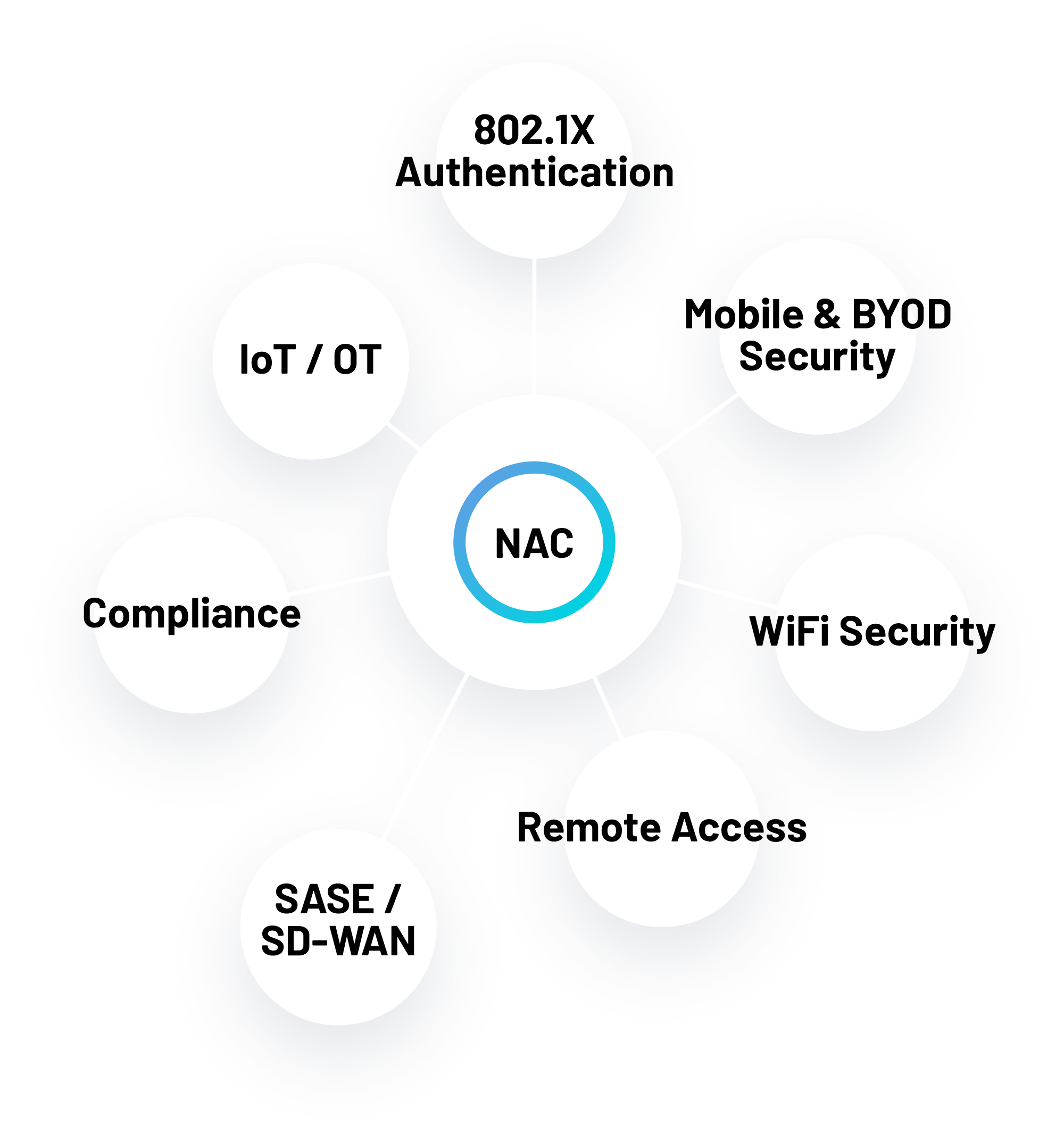
We've Got You Covered,
No Matter the NAC Use Case
Whether you need to secure remote VPN access, guest WiFi networks, or on-site wired ports – Portnox can help you implement actionable access control, risk assessment and device remediation policies for managed company devices, BYOD, IoT/OT and more.
Trusted Across Industries
Portnox's network access control solutions are utilized by hundreds of enterprises all around the world across an array of industries.






Looking for a Modern VPN Replacement? Look No Further. Portnox ZTNA is Here.
For decades, the VPN has been the slightly-too-proud workhorse of remote access—trudging along, sweating profusely, slowing everything down, and occasionally taking a nap in the…
Portnox Unleashes Fast, Frictionless, Cloud-Native ZTNA
Secure Access, Simplified. No Agents, No Clients, No Passwords—No Problem. AUSTIN, TX, July 8, 2025 — Portnox, a leading provider of cloud-native access control…
Try Portnox CLEAR for Free Today
Get started with a free trial and gain access to all of Portnox CLEAR’s powerful NAC capabilities!