The proliferation of Bring Your Own Device (BYOD) policies has revolutionized the way businesses operate. While the BYOD trend offers flexibility and convenience for employees, it also presents a myriad of security challenges for enterprise networks. As Chief Information Security Officers grapple with the increasing complexity of cybersecurity risks, understanding and addressing BYOD security issues has become a top priority. In this blog post, we will delve into some of the most pressing BYOD security issues facing enterprise networks today and explore strategies to mitigate these risks effectively.
Unveiling the Core BYOD Security Challenges
The advent of BYOD policies has undeniably broadened the horizons of workplace flexibility and efficiency. However, it simultaneously ushers in a complex array of security vulnerabilities. A predominant challenge lies in the disparate nature of personal devices, which complicates the enforcement of uniform security measures. This variability not only strains the implementation of comprehensive security policies but also paves the way for potential exploits by adversaries seeking to infiltrate the corporate network.
Moreover, the risk of data leakage and loss looms large in a BYOD-centric environment. Personal devices, inherently less secure than corporate-issued hardware, become potent vectors for the unauthorized dissemination of sensitive information, should they fall prey to theft or misplacement. This scenario poses a formidable threat, undermining the integrity of corporate data and potentially catapulting the organization into a maelstrom of legal and financial repercussions.
Addressing these challenges necessitates a nuanced understanding of the intricacies of BYOD security, a commitment to evolving security practices, and a strategic framework designed to safeguard the digital frontier of the enterprise.
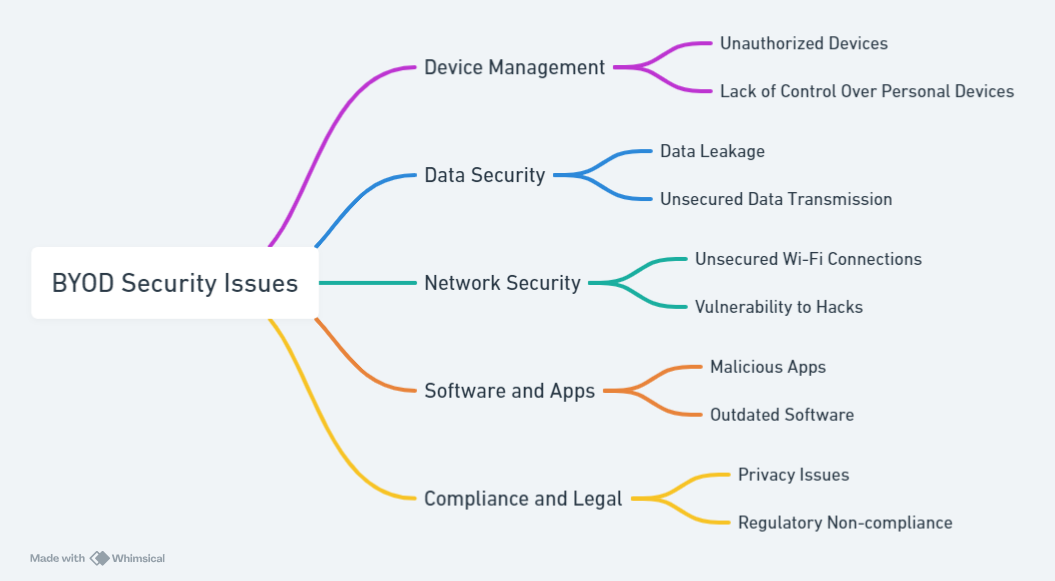
Mitigating BYOD Risks Through Strategic Planning and Policy Design
Mitigating the risks associated with BYOD requires a nuanced strategy that prioritizes security without compromising the flexibility and productivity that BYOD policies afford. To effectively navigate the challenges, it is essential for organizations to craft comprehensive BYOD policies that delineate clear boundaries and expectations for device use. These policies should underscore the significance of data encryption, outline acceptable use policies, and detail the security requirements for devices connecting to the corporate network.
A pivotal aspect of a robust BYOD strategy involves the cultivation of a security-first culture within the organization. This is achieved through regular, targeted training sessions and awareness programs aimed at educating employees on the critical role they play in safeguarding corporate data. Such initiatives not only empower employees with the knowledge to recognize and mitigate potential threats but also foster an environment where security considerations are seamlessly integrated into daily operations.
Implementing a strategic approach to BYOD, underscored by well-defined policies and a commitment to employee education, positions organizations to leverage the benefits of BYOD while effectively managing the associated security risks.
The Crucial Role of Network Access Control (NAC) in BYOD Security
In the intricate landscape of BYOD security, the implementation of Network Access Control (NAC) emerges as a linchpin in fortifying enterprise networks against potential vulnerabilities. NAC empowers organizations with the capabilities to meticulously authenticate and scrutinize devices at the point of entry, ensuring that only compliant and authorized devices gain network access. This system of gatekeeping is instrumental in maintaining a secure network perimeter, effectively mitigating the risks introduced by the diverse array of personal devices interfacing with corporate resources.
By harnessing NAC, organizations gain a robust framework for policy enforcement, allowing for the dynamic assessment and management of devices based on predefined security criteria. This strategic alignment enables the seamless identification of non-compliant devices, facilitating prompt remedial actions to address security concerns without hampering the user experience. The ability of NAC solutions to provide comprehensive visibility into device activity on the network further enhances the security team’s capacity to detect and neutralize threats in a timely manner, thereby safeguarding sensitive corporate data against unauthorized access and potential compromise.
In essence, the deployment of NAC is a critical step towards achieving a secure BYOD environment, bridging the gap between the demand for flexibility and the imperative of security.
Beyond NAC: Embracing Comprehensive BYOD Security Measures
While Network Access Control (NAC) stands as a foundational pillar in securing enterprise networks from BYOD-related vulnerabilities, it represents only a segment of the broader cybersecurity spectrum that demands attention. To construct a resilient defense mechanism against an ever-evolving array of cyber threats, the integration of endpoint security solutions becomes imperative. These systems offer additional layers of protection by preventing malware infections and providing critical security updates across all devices.
Equally important is the deployment of Mobile Device Management (MDM) software. This technology enables precise control over how devices interact with corporate networks and data, allowing for the remote wiping of data in case of device loss or theft, thus significantly mitigating potential data breaches.
Furthermore, the significance of data encryption cannot be overstated. Encrypting data at rest and in transit ensures that, even in the event of interception, the information remains unintelligible and secure from unauthorized access.
Incorporating these comprehensive security measures, alongside regular security posture assessments and proactive vulnerability management, forms a robust security infrastructure capable of withstanding the complexities introduced by BYOD. This holistic approach not only enhances the security landscape but also fosters an environment where innovation and productivity can flourish, unhampered by the specter of cyber threats.
The Future of BYOD Security: Predictions and Preparations
As the landscape of work and technology perpetually shifts, the trajectory of BYOD security strategies is poised for significant evolution. The burgeoning integration of remote work dynamics and the pervasive spread of the Internet of Things (IoT) devices signal a broadening attack surface, necessitating a forward-thinking approach to cybersecurity defenses. Anticipation of these shifts underscores the need for innovative security frameworks, harnessing the potential of artificial intelligence (AI) and machine learning to refine and strengthen BYOD security protocols. Such advancements promise not only to enhance the detection and mitigation of threats but also to streamline the adaptability of security measures in real-time. Embracing these technological strides will be crucial for organizations aiming to stay ahead in the cybersecurity arena, ensuring robust protection against the sophisticated cyber threats of tomorrow.
Try Portnox Cloud for Free Today
Gain access to all of Portnox's powerful zero trust access control free capabilities for 30 days!




