Cloud Security
As your organizational threat surface grows in size, scope and complexity, the adoption of cloud security tools is key to maintaining a secure status quo.

The adoption of cloud technologies is one of the fastest-growing trends in IT.
As businesses respond to fast-evolving customer needs, shifting business models and changes in the work setup, agility and elasticity are two primary drivers that will exponentially boost cloud adoption across organizations of all sizes. The transition to the cloud, however, poses a new set of challenges for IT security professionals.
What is Cloud Security?
Cloud adoption is an IT security strategy that is disrupting industries around the world. The move to the cloud provides convenience, lower total cost of ownership, and consistent uptimes compared to on-premises infrastructure. As a result of the benefits available from cloud migration, it’s expected that spending on public cloud infrastructure and services will grow to $500 billion by 2023.
When it comes to cybersecurity, cloud security (or cloud computing security) spans policies, practices, and technologies for protecting cloud computing systems. In essence, cloud security fundamentally secures cloud-stored data and other digital assets against data breaches, malware, distributed denial of service (DDoS), hacking, and other cybersecurity threats.
With cloud security, end-users expect their data to be more secure in the cloud than on their hard drives or local servers. Though cloud service providers have cybersecurity measures in place, that doesn’t mean they are invulnerable to data breaches, DDoS, and other cybersecurity threats.
Why is Cloud Security Important?
So, why is it that so many companies are turning to the cloud, particularly for security? Well, the this questions yields a variety of interconnected answers:
- Security Centralization: Cloud security can provide the functionality of traditional IT security while letting customers enjoy the advantages of cloud computing securely and privately. As the cloud centralizes apps and data, the cloud provider can centralize protection and streamline its monitoring process. It’s also easy to perform recovery as the cloud provider can manage everything from one place.
- Total Cost of Ownership (TCO): The cloud eliminates the need to buy and manage on-premise hardware.
- Reliability & Ease-of-Use: With cloud security technologies in place, cloud customers can safely access their data and applications – no matter their location or device type.
In general, companies can’t take advantage of the many benefits of the cloud while maintaining their security posture without adequate security measures for cloud-based applications and a growing volume of data residing in the cloud.
How Does Cloud Security Work?
Traditionally, networks had no means of ensuring that its servers were fully protection. Today, with cloud web security, traffic gets to the cloud instead of being routed to the servers directly. The cloud analyses the traffic and only allow the legitimate users to gain access. Any traffic that the cloud does not approve, it blocks it from getting to the server.
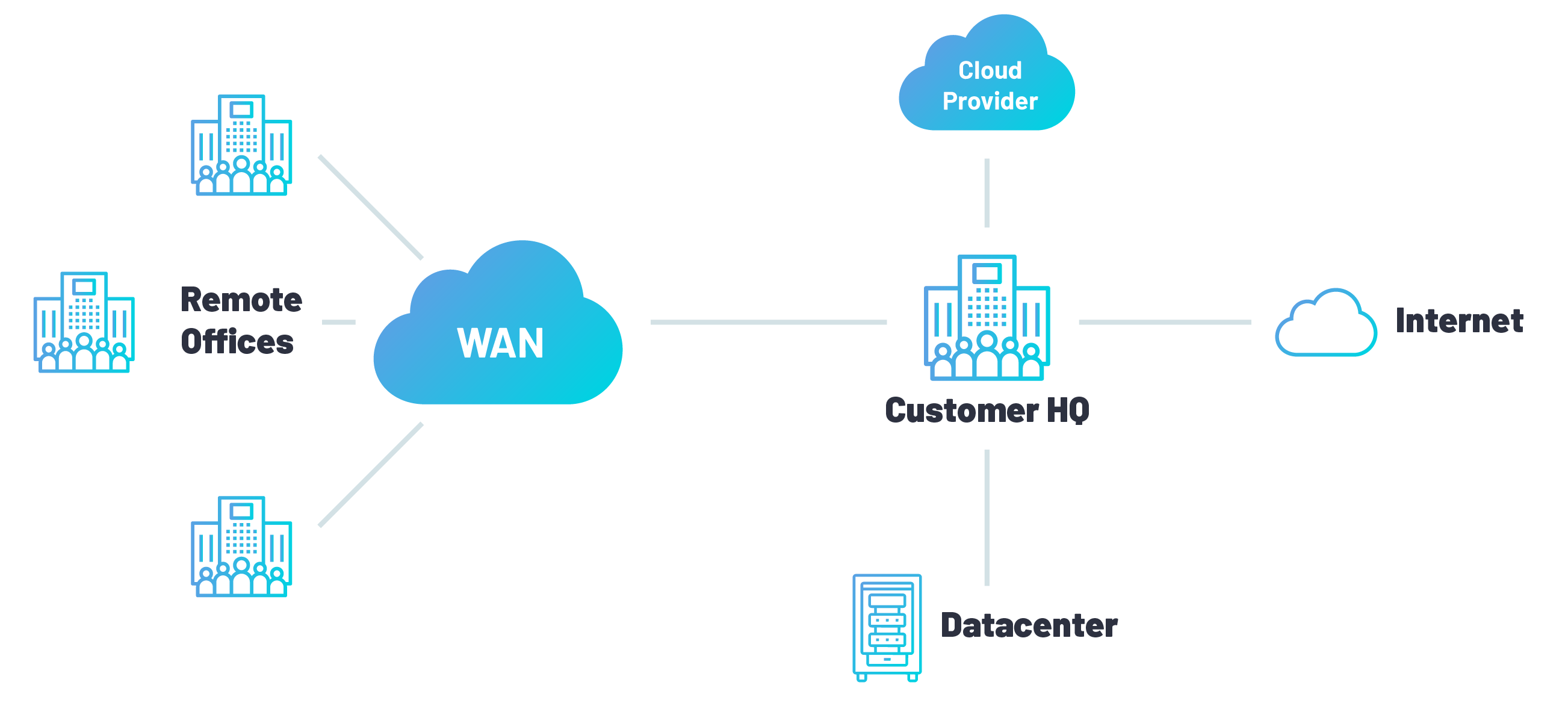
On-premise applications filter data before it reaches the server, often making them hard and costly to maintain over time. They filter traffic after it reaches its network. Sometimes the machines get overwhelmed and may shut down to block both good and bad traffic, and they may not serve the intended functions. With cloud security solutions, traffic is typically redirected to the security cloud first, where it gets filtered before reaching the respective application.
Cloud Security & Network Access Control
Nearly primary management and productivity tool used by businesses have shifted to the cloud. Network access control is no exception. The inherent productivity, operational, economic, and accessibility benefits have driven this trend in the last fifteen years. When it comes to NAC, however, there is a big difference between cloud-based and cloud-delivered.
Cloud-Based v. Cloud-Delivered
Today, almost all NAC vendors offer an accessible cloud-based (or managed) platform from which to manage network access, but this typically still requires on-site hardware to be installed. A cloud-hosted NAC environment is generally the “on-premise” software hosted on dedicated servers and managed by the vendor on behalf of the customer. These are effectively on-premise applications that are available remotely.

Contrary to cloud-based applications, cloud-hosted applications are generally not designed to be hosted as multi-tenant instances and can come with several challenges:
- Initial implementation times are longer due to server setup, software installation, and customization.
- Upgrades are manual and specific to each server (not all customers are upgraded simultaneously), causing customers to be “stuck” or “locked-in” to older versions of the product while they wait for the vendor.
- Expansion may require the purchase and setup of additional hardware because software is hosted on dedicated servers by the vendor.
With a cloud-delivered approach to NAC, however, you stand up everything from a RADIUS server in the cloud to allow for centralized authentication and authorization up to certificate authority, resulting in:
- Implementation times that are much shorter as no additional hardware or software installation is required – customer access occurs almost “instantaneously” without delays;
- Shared code base enables quicker, faster upgrades (all customers are upgraded at once since it is single instance / multi-tenant with a single upgrade event from the vendor);
- Seamless, dynamic expansion of computing resources to scale with usage and/or users
What is the Future of Cloud Security?
Cloud Security Consolidation
As we move into the 2020s, you can expect to the cloud native security platforms (CNSPs) market to expand. These platforms will enable cybersecurity teams to manage all of their security across public, private and hybrid clouds from a single console. Siloed security solutions will be integrated into these comprehensive platforms: capabilities such as network access, governance and compliance, threat detection and response, data loss prevention and beyond will all live in a single pane of glass.
Security Vendor Consolidation
As multi-cloud strategies grow in popularity, we’re seeing an increase in visibility issues. Moving forward, cybersecurity teams will continue to search for ways to gain the level of visibility they once enjoyed on-premises. Traditionally, cloud native resources have made visibility difficult, but new security platforms that leverage proprietary cloud provider APIs offer richer context for cloud-based workloads.
All Hail, SASE
SASE, pronounced “sassy”, stands for Secure Access Service Edge. It is a cloud-based network security model and category, proposed by Gartner in 2019, to support agile secure access to enterprise assets. This model includes the network security solutions in a global and cloud-native service that allows IT teams to easily connect and secure all of their organization’s networks and users in an agile, cost-effective, and scalable way. This is especially useful in the currently globally dispersed digital enterprise.
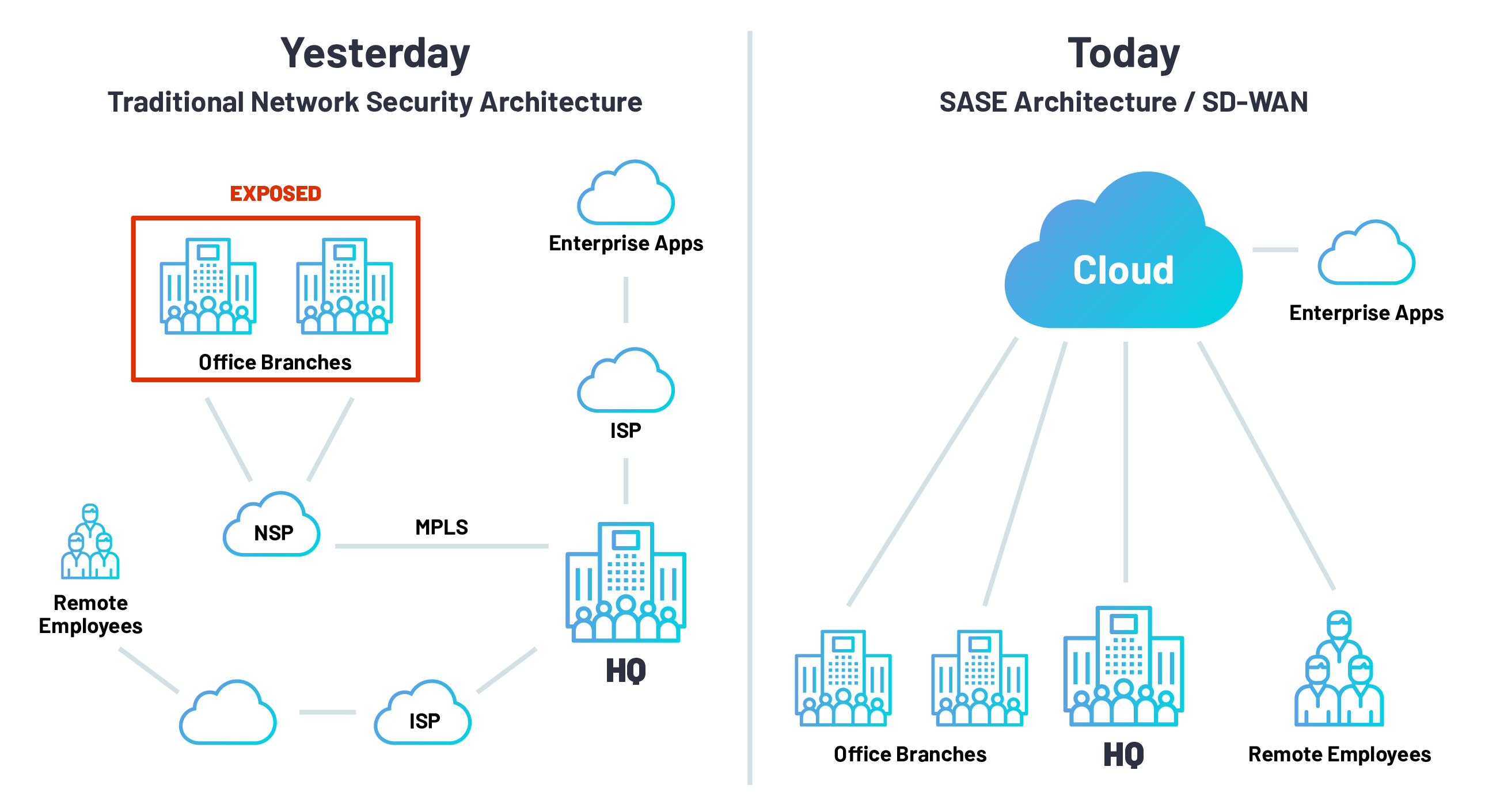
The sensible course of action is to plan a security strategy to be scalable and efficient in the present, while at the same time future-proofing the organization’s security. With the organizational data migrating to the network edge, it makes sense to authenticate and authorize users and devices in a cloud format, thereby assuring that regardless of the equipment and geolocation, employees can securely connect in a cost-efficient and secure method to the needed resources.
Related Updates
Try Portnox Cloud for Free Today
Gain access to all of Portnox's powerful zero trust access control free capabilities for 30 days!